Why leaning on personal phones for MFA is becoming a blind spot – and how TypingDNA Verify 2FA closes it
1. The hidden dependency: personal phones as the second factor
Only 15 % of companies still issue a work smartphone; everyone else depends on BYOD or a hybrid model (jumpcloud.com). When security teams roll out SMS codes or authenticator apps, they quietly move three critical controls onto devices the company neither owns nor can audit:
- OS patching and hardening
- Physical possession of the factor (lost, stolen, or handed to someone else)
- User consent to install and maintain security software
2. Why personal phones cannot be audited or secured
- 28 % of smartphone owners use no screen lock at all (pewresearch.org).
- 90 % of Android phones still run an outdated OS, missing critical security patches (ctctechnologies.com).
- 41 % of adults have shared at least one account password with friends or family, showing how often devices and credentials are informally shared (pewresearch.org).
- 49 % of employees let friends or family use a work-enabled mobile device (copperbandtech.com), and 23 % openly share the device passcode itself (allaboutcookies.org).
Because the hardware is private property, IT cannot force updates, install an EDR agent, or preserve forensic evidence after an incident. The result is an authentication factor the enterprise can neither test nor trust.
3. Compliance is closing the loophole
- PCI DSS 4.0 makes strong MFA mandatory for every account that touches payment data by 31 March 2025 (blog.pcisecuritystandards.org).
- The HIPAA Security Rule update proposed for 2025 explicitly warns about risks from unmanaged mobile devices (federalregister.gov) and converts MFA from a flexible option to a required control across all systems that handle ePHI (reuters.com).
Auditors increasingly flag “personal phone” as a gap, because the organisation cannot prove the factor’s integrity or possession.
4. The hidden cost of phone-based MFA
Security is already the top obstacle to BYOD adoption for 30 % of IT leaders (jumpcloud.com). Add device loss logistics, SMS fees, roaming charges, reset tickets, and stipend disputes, and the financial upside of BYOD quickly disappears—especially after the first breach investigation.
5. Old alternatives fall short
Hardware tokens remove the phone but create inventory headaches and replacement delays. Passkeys often still rely on a “trusted” personal device. Neither solves the audit-and-control problem that regulators now spotlight.
Desktop passkeys and authenticator apps such as Okta Verify/Okta FastPass are simply not compliant (blog.typingdna.com)
6. A phone-free path: TypingDNA Verify 2FA
Verify 2FA eliminates the phone entirely by turning the way a user types on any desktop keyboard into the “something-you-are” factor:
- Nothing to carry or install – users enrol and verify just by typing four words.
- Corporate control – typing patterns are stored and verified inside the enterprise environment, so every login is fully logged and auditable.
- Lower total cost – no SMS fees, no hardware shipping, far fewer help-desk resets.
- Regulation-ready – meets MFA frameworks without exposing data to unmanaged personal devices.
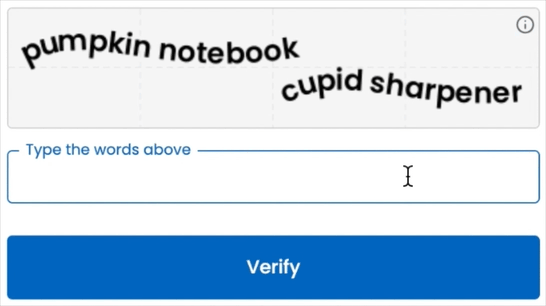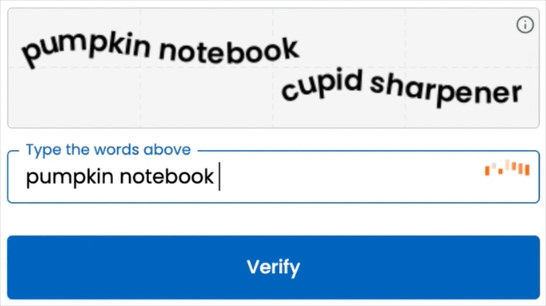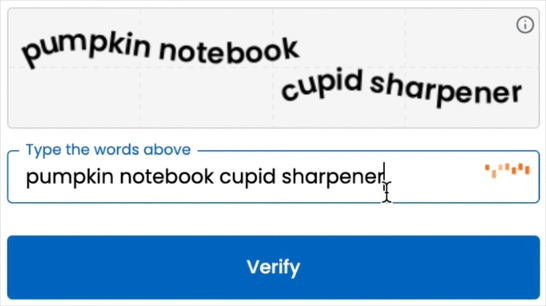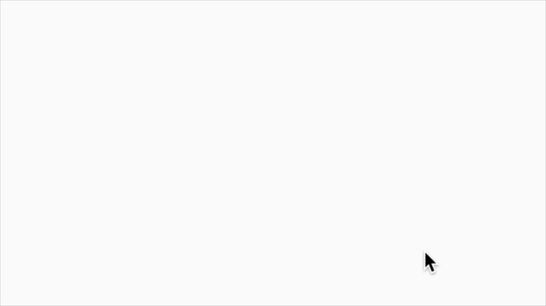
Want to see the difference?
Contact us for a 30-day pilot and experience MFA that works—without a phone in sight.