Factors in a 2FA solution have drastically evolved since the mid-’90s. As we know it in 2021, account protection has developed due to increased attention from security departments over the past years. More sophisticated attacks on business and consumer accounts have led to increased demands for better security policies.
Not only are companies concerned about protecting their employees’ or customers’ accounts, but also regulations have been enforced to create a unified approach towards security. On top of that, the Covid-19 sanitary restrictions’ forced digitalization led to various factors included in the best 2FA solution.

Table of contents:
- Two-Factor Authentication (2FA) in 2021
- 2FA solution implementation across various online platforms
- What is the best two-factor authentication solution?
- 2FA solution implementation examples
- Conclusion
Two-Factor Authentication (2FA) in 2021
Sophisticated cybersecurity attacks have increased 2FA awareness and adoption. As a result, in 2021, more than 70% of individuals worldwide use 2FA to log in to their favorite apps. The main contributor to this high adoption rate has been the increased number of US adults who have been victims to account takeover, more than 20%. Additionally, the growth of identity and account takeover fraud is fueled by the advancements of bots capable of performing upwards of 100 attacks per second—essentially supporting limitless account takeover.
Although recognized as a basic security measure, 2FA isn’t necessarily welcomed by consumers, especially if the involved factors create a burdensome user experience. For example, a 2020 study shows that 23% of respondents found SMS one-time passwords to be very inconvenient, while 56% who use a smartphone or other personal device to access work-related items don’t use 2FA.
A more user-friendly approach is desired, and typing biometrics-based authentication is the go-to authentication factor, especially since the authentication is in band and users don’t need to switch devices or input any codes sent via SMS. 87% of consumers say they’ll be comfortable with using biometric authentication soon.

Security frameworks and regulations
Regulating security and demanding the best 2FA solution has seen a rise in the past decade. Institutions and governments have come together to impose better security policies and standards on global levels. Therefore, today we see not only the BFSI environment highly regulated, but NIST recommendations are also in place for most companies handling sensitive or personal data. From their architecture to the user interface and authentications, products must be designed with privacy and security-first approach. In addition, since too many breaches are a result of poor account protection, most companies today offer increased account security, starting with the log-in process.
Covid-19 as a driver for better authentication
In the Covid-19 era, organizations have had to rapidly adjust to working and learning from anywhere. Customers, employees, or even patients have also quickly adapted to the new digital interaction. Various businesses, from shops to banks and healthcare organizations have moved online. Companies moving online have swiftly implemented the most accessible and easy to deploy identity and transaction verification methods to remain competitive.
Has the pandemic contributed to better 2FA solutions?
The digital interaction with clients, employees, or patients driven by the pandemic has been challenged, particularly by identity confirmation and fraud around user identity verification. However, almost two years later, with the digital shift already in progress, the pandemic was a driver for companies to implement a 2FA solution relying on secure authentication coupled with a frictionless user experience.
2FA solution implementation across various online platforms
Since relying on a single factor to authenticate users belongs in the past, companies have started juggling with multiple authentication factors to implement and create the best 2FA flows.
What are the three types of authentication? The three generally recognized factors for authentication are based on:
- Something you know (such as a password or PIN)
- Something you have (such as a hardware token or smartphone)
- Something you are (such as biometrics like fingerprint, or faceID, or behavioral like your typing patterns).
A 2FA solution combines two of the above options. The most common two factors are username and password and a numerical code sent via a simple text message.
What is the best two-factor authentication solution?
The best 2FA solution deploys secure, and user-friendly authentication factors such as biometrics like fingerprint or faceID (something you are as a factor), SMS OTP or authenticator apps (something you have) or secrets, and a PIN (something you know).
Also, a transition to more user-friendly and inclusive factors is seen among the biggest players in various industries. Authentication technologies are evolving to be inclusive and respond to an increasing and diverse global user base: 2FA solutions now use technology adapted for visually impaired individuals adding a text-to-speech factor or paying attention to users who don’t own a smart device.
2FA solution implementation examples:
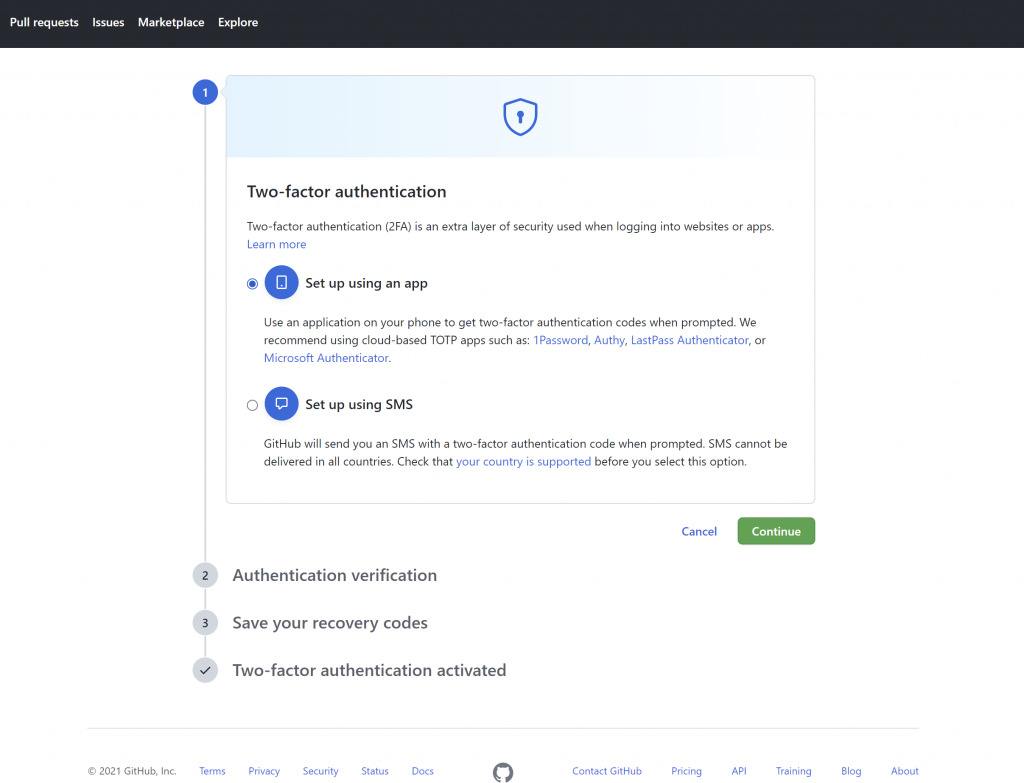
Github
Github is the largest development platform where more than 5 million developers and 3 million companies build, ship, and maintain their software. Securing access to such sensitive information as the code of core products is crucial. Github offers a multitude of MFA options, including cloud-based Time-based One Time Password (TOTP) apps such as various authenticator apps or SMS OTP.
GitHub 2FA options for account protection
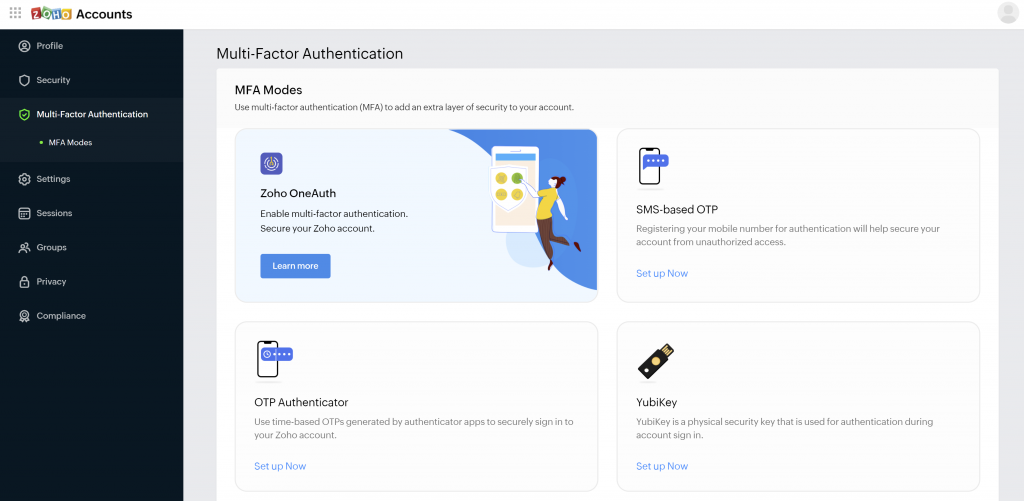
Zoho
Zoho is a software suite and SaaS application that addresses various needs for businesses of all sizes. The platform offers solutions ranging from HR software, sales, accounting software, and CRM.
Secured authentication is critical given the sensitive nature of the business information provided to use the Zoho solutions. Still, with such a variety of use cases covered, the targeted users will be of various ages and technology education levels. Therefore, implementing a 2FA or MFA solution that is inclusive and user-friendly is key for their audiences. Zoho offers a multitude of authentication options, with various grades of security ranging from their own mobile authentication app, SMS OTP, Yubikey, and other authenticator code-generating apps.
Zoho 2FA options for account protection
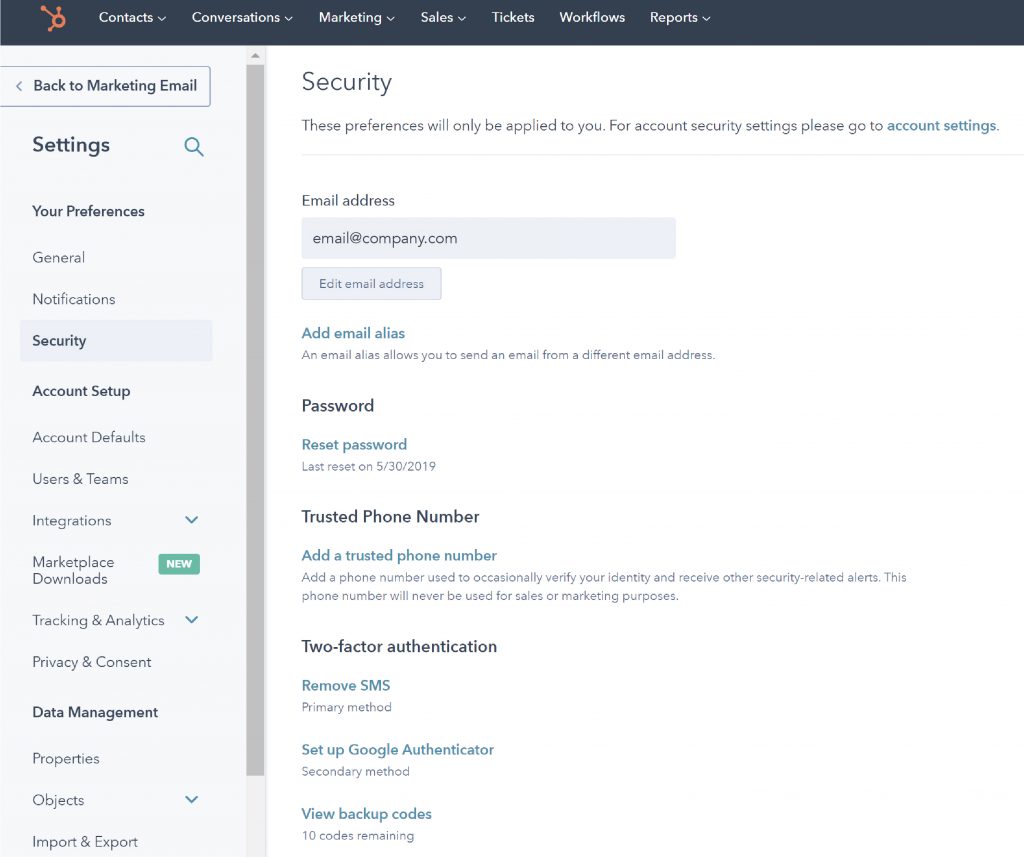
Hubspot
Hubspot was founded in 2005 and was one of the first companies to promote the concept of inbound marketing as a strategy to convert leads into customers. Hubspot’s features have diversified and are now used by millions of users. Services ranging from sales tools to marketing and reports offer an extensive palette of tools. 2FA options were introduced in July 2019, and now, admins can even require two-step verification for account users.
Hubspot 2FA options for account protection
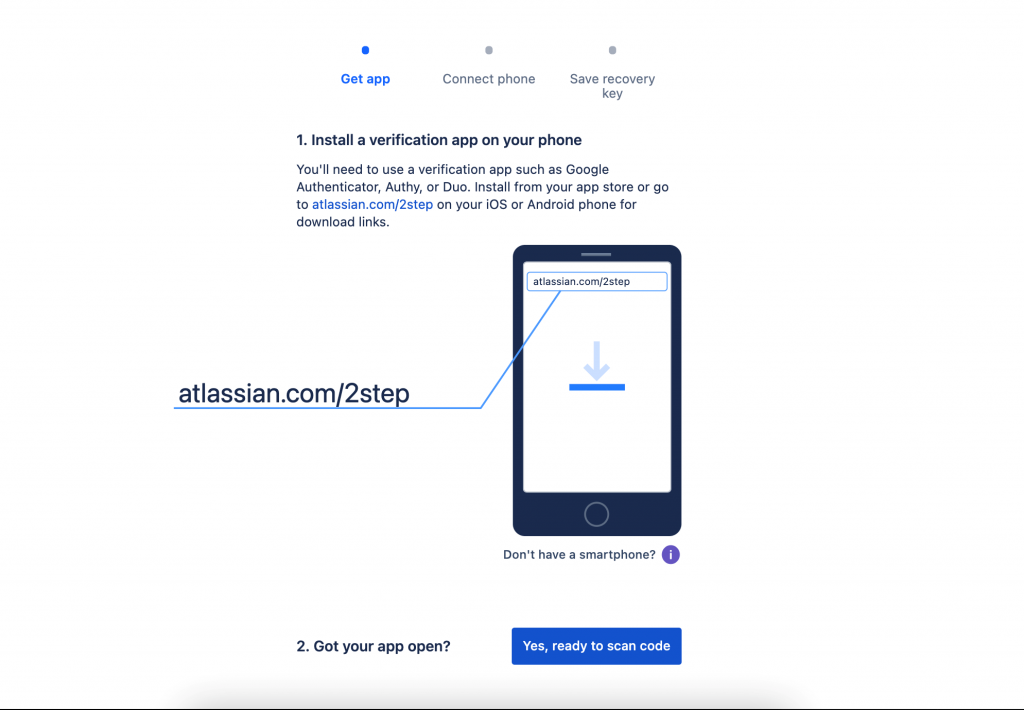
Jira by Atlassian
Atlassian holds one of the most popular tools used by development teams around the world. Among them are Jira and Trello. More than 200,000 companies use the software tools to create products, practices, and team collaboration. Although a company account on Jira would not typically offer access to code, a hacked account transfers enough data for an attacker to understand sensitive information about the development phase of a particular product. Therefore, deploying the best 2FA solution is critical to secure authentication.
Jira users can enhance security by enabling a 2-step verification composed of SMS OTP’s or various authenticator apps like Google Authenticator and Authy Duo Mobile. Admins can also enforce 2FA authentication and two-step verification for accounts that are used by scripts or services to access Atlassian Cloud REST APIs; API tokens are recommended.
Jira 2FA for account protection
Conclusion
In 2021, the 2FA solution implemented by industry leaders deploys various authentication factors ranging from SMS and Email OTP to authenticator apps. But, unfortunately, we still see a gap between security and ease of use or accessibility. The authentication factors used are focused on security needs but mostly disregard user experience.
TypingDNA Verify 2FA as an alternative to SMS OTP or authenticator apps
An alternative to SMS OTPs or authenticator apps is TypingDNA Verify 2FA, which is focused on in-band authentication. The technology does not require a device or specialized hardware to receive a code. Instead, using state-of-the-art technology, TypingDNA Verify 2FA authenticates users based on how they type on their keyboards. Instead of reaching for their phones and unlocking them to open an authenticator app, the secure approach from TypingDNA only requires users to type four short words in the same app they’re logging into.
This is also a faster authentication method, reducing the users’ effort and improving their experience.
Watch the video below to see how SMS OTP authentication compares to TypingDNA Verify 2FA.
Try this live demo to see for yourself how seamless authentication with TypingDNA Verify works in real-time.