Updated June 2025

To achieve security, enterprises work with IAM systems that deploy multi-factor authentication (MFA), or simply two-factor authentication (2FA). MFA allows businesses to verify their employees’ identities when they log in to corporate apps.
While MFA is key to security, companies should avoid using methods that require employees to use their phones.
Below, we focus on why phone-based MFA is burdensome and costly for companies and employees. And we highlight typing biometrics—especially with TypingDNA Verify 2FA—as a seamless and privacy-focused alternative for workforce authentication that doesn’t rely on personal phones.
Why is workforce MFA the new normal?
With increased cybersecurity threats and more people working remotely, enterprises rely on identity and access management (IAM) providers to secure workforce access to corporate data and apps.
IAM providers such as Okta, Ping Identity, Microsoft Entra ID, ForgeRock, and Keycloak offer services that enforce security within a company’s network. These providers help companies implement robust security flows that do not hinder employee productivity.
To keep data safe, enterprises use MFA to verify the identity of users attempting to log into the corporate network. And although most MFA/2FA methods increase security, some offer better UX and compliance outcomes than others.
Before we explore why typing biometrics is a better choice, let’s look at why phone-based authentication methods are quickly becoming outdated.

Why using personal phones for MFA/2FA is a thing of the past?
Let’s say employee Jane is trying to log in to the corporate network to access the data she needs. Most IAM systems begin with Jane entering her username and password. Then, she must confirm her identity by entering a one-time passcode (OTP) sent via SMS.
Even companies that avoid SMS still require phones—for apps like Google Authenticator or Microsoft Authenticator, push notifications, or voice calls.
Phone-based authentication burdens both employees and employers. Many employees are uncomfortable using personal phones for work. For employers, this translates into privacy concerns, operational complexity, and cost. In some jurisdictions, companies may even be obligated to cover phone-related expenses.
It’s clear that asking employees to use personal phones for MFA is no longer practical—or defensible.
Enter behavioral biometrics: authentication methods that don’t require a phone
Among behavioral biometrics, typing biometrics and voice recognition are most popular. However, voice-based solutions often require a microphone or phone call.
Typing biometrics, by contrast, works directly with the keyboard. No phone, token, or special hardware is needed. Typing biometrics analyzes how a person types to recognize and authenticate them—making it ideal for enterprise use.
MFA/2FA with typing biometrics explained
In a workforce setting, TypingDNA Verify 2FA uses a 4-word dynamic phrase that employees type during login. The system compares how those words are typed to the user’s stored typing pattern.
Returning to Jane’s example: if her company uses TypingDNA, after her initial login, she’ll be prompted to type a 4-word phrase like “hospital shampoo teapot rainbow.” TypingDNA uses this to instantly verify Jane based on her typing signature.
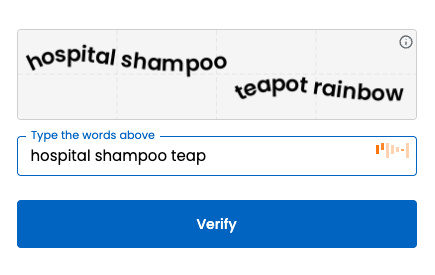
This all happens within the browser, and the entire process takes under 5 seconds.
Benefits of typing biometrics for workforce authentication
TypingDNA Verify 2FA enables:
- ✅ Authentication with existing keyboards
- ✅ No BYOD / No personal phones
- ✅ Quick, seamless user onboarding
- ✅ Support for most IAM platforms through OIDC integration
Ready to improve your workforce MFA/2FA experience with typing biometrics?
TypingDNA offers this technology in the form of an OIDC integration for major IAM platforms, (or for some platforms as a custom integration).
To learn more and get a quote for our TypingDNA Verify 2FA (OIDC version), available for Okta, Ping Identity, Microsoft Entra ID, ForgeRock, Keycloak, and more contact us.