Windows Defender for Endpoint and similar antimalware/antivirus systems are all pretty good at analyzing incoming cyber threats that target endpoints, and responding to virus threats. But, what these systems fail at is providing visibility into whether the employee you trusted with that company endpoint is the one who’s actually accessing it throughout the entire workday — especially if your workforce is working remotely and out-of-sight.
Because employees increasingly work from home, your company’s endpoints have a higher chance of ending up in the hands of unauthorized users. But, unlike the device’s authorized owner (the employee), household members and friends are untrained in your company’s security practices — placing your organization and devices at greater risk of data breaches.
The question becomes:
- Do you trust your remote workforce to be vigilant about never allowing the company device to end up in the hands of an unauthorized user?
- More importantly, are you willing to bet your customer’s trust on their data staying secure when employees work from home?
Below, we’ll explore why devices are frequently shared in remote environments, and what companies can do to prevent device sharing. We’ll also explain what situations Windows Defender for Endpoint is good for, what it does — and also what it can’t do. Lastly, we’ll demonstrate how you can bridge the security gaps left behind by Windows Defender for Endpoint by adding continuous endpoint authentication to your company computers.
TABLE OF CONTENTS
What is Windows Defender for Endpoint?
What can Windows Defender for Endpoint do?
What can’t Windows Defender for Endpoint do? And the security gaps you must be aware of.
How ActiveLock bridges the security gap missed by Windows Defender for Endpoint
What is endpoint security?
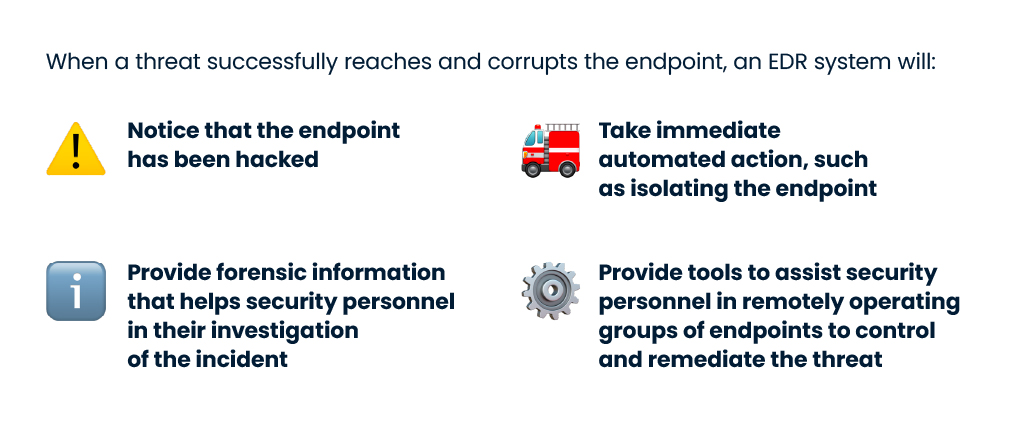
Endpoint security solutions protect against sophisticated cyber threats, with the most complex ones offering protection and performing adaptive security architecture tasks such as hardening, incident detection, and response. Any Endpoint Detection and Response (EDR) solution is built on the premise that the endpoint will be compromised at some point. EDR works as an active security solution that can detect and investigate security vulnerabilities, but also restore endpoints to their pre-infected status. Learn more about EDR.
While EDR solutions focus on detection & response, Endpoint Protection Platforms (EPP) focus on malware detection & other measures that help mitigate endpoint threats. EPPs commonly provide tools such as Antivirus and Next-Generation Antivirus (NGAV), personal firewalls protecting endpoints, data encryption, and data loss prevention.
Although an antivirus may provide good protection for a database of known threats, when it fails the organization loses visibility into what is happening on the endpoint, and security personnel are unable to access the endpoint instantly to resolve the breach. That’s precious lost time when every second counts.
EDR on the other hand includes real-time monitoring and detection of threats – including those that may not be easily recognized or defined by a standard antivirus.
What is Windows Defender for Endpoint?
Windows Defender for Endpoint (also known as Microsoft Defender for Endpoint) is a solution developed by Microsoft to prevent, detect, investigate and respond to a broad range of security threats within enterprise networks and across end-user devices — including tablets, cellphones, laptops, servers, and more.
In 2005, at the RSA Security Conference, Bill Gates announced that the beta version of Microsoft Defender for Endpoint — then named Microsoft AntiSpyware — would be free for all users with a valid license for Windows 2000, Windows XP, and Windows Server 2003 operating systems.
Microsoft Defender for Endpoint had various names throughout the years and was most commonly tagged as “Windows Defender” for most of the time. Today, Microsoft Defender for Endpoint has grown to do a good job of detecting malware files, blocking exploits and network-based assaults, and pointing out phishing websites.
What can Windows Defender for Endpoint do?
An organization’s network can reach thousands, if not tens and hundreds of thousands of devices when you take into account the growing popularity of BYOD (bring your own device) practices and increased application of IoT (internet of things) across physical devices. Any of those devices that are connected to a network are called endpoints and bring up a series of security risks that require organizations to take proactive measures in preventing breaches.
Microsoft Defender for Endpoint protects endpoints against advanced attacks by offering preventive security, post-breach detection, automated investigation, and reaction to potential security risks or breaches.
Some of its core features include:
- 🎯 Attack surface reduction: its rules are designed to target certain program actions such as launching executable files and scripts that attempt to download or run files, executing obfuscated or otherwise suspicious scripts, or performing actions that applications do not normally initiate during typical day-to-day operations.
- ⛔️ Block at first sight: is a threat protection component of next-generation cybersecurity that identifies and blocks new threats in seconds.
- 🛡Controlled folder access: protects your critical data from rogue programs and dangers like ransomware.
- 🔒 Exploit protection: is an anti-malware software that protects users of the Windows 10 operating system from intrusions. Exploit Guard is included in Windows Defender Security Center and may defend devices from a variety of attacks.
- 🌐 Network protection: is a new Windows Defender security feature released by Microsoft in the Fall Creators Update for their Windows 10 operating system It complements Windows Defender SmartScreen by limiting outbound (HTTP and HTTPS) traffic to resources with a poor reputation.
- 🕵️ Potentially Unwanted Application detection: it detects Potentially Unwanted Applications (PUA), which are a category of software that can cause your machine to run slowly, display unexpected ads, or at worst, install other software which may be more harmful or annoying.
- ☁️ Cloud-delivered protection: is a type of security system that is meant to secure essential infrastructure, apps, and data in the cloud rather than on-premises.
- 💻 Microsoft Defender SmartScreen: it guards against phishing or malware websites and programs, as well as the download of potentially harmful files. Microsoft Defender SmartScreen assesses whether a site is possibly harmful by analyzing visited webpages for signs of unusual activity.
These features are complemented by robust APIs that provide access to and integration with Microsoft’s endpoint security platform. Microsoft Defender for Endpoint can be compared against other solutions by looking at competencies categories such as evaluation and contracting, integration and deployment, service and support, and specific product capabilities.
According to Gartner, some competitors and alternative EDR platforms to Microsoft Defender for Endpoint are Singularity Platform, Falcon, Trend Micro XDR, Harmony Endpoint, VMware Carbon Black EDR, Symantec Advanced Threat Protection, Malwarebytes Endpoint Detection and Response, and Cortex XDR.
However, none of these solutions can promise that only the authorized employee is using your company devices, as, just like Microsoft Defender for Endpoint, they don’t continuously authenticate the user throughout their interaction with the company computer. Instead, once users have logged into the computer at the beginning of their working day, they receive implicit trust that they won’t share the unlocked device with anyone else. A security gap that can be dangerous, particularly when employees and contractors work out-of-sight in remote environments.
While implementing antimalware systems such as Windows Defender for Endpoint is crucial in protecting data, companies should be more careful with how much trust they offer their employees, especially in work-from-home environments. The risk of data breaches and compliance violations increase when the employee shares their device with friends, family, or any other unauthorized users.
The good news is, there’s a way to mitigate these risks. Periodically verifying employees’ identities only once at log-in or at the beginning of their workday is not enough. Instead security teams must adopt a zero-trust philosophy using continuous endpoint authentication of employees’ to make sure only the rightful owners access company devices at all times.
What can’t Windows Defender for Endpoint do? And the security gaps you must be aware of.
Because attackers can exist both inside and outside the network, no user should ever be completely trusted at any time — even if they successfully verified themselves at the front door with a username and password. The problem is, antimalware defense applications can’t actually distinguish who the person using the computer is after login, and therefore can’t ensure that an organization’s systems are accessed solely by authorized users at all times. This is a critical gap which presents a large risk in work-from-anywhere environments.
Remote work has brought a change in the way employees interact with their devices. In remote environments, laptops and computers left unlocked and unattended have a much higher chance of being used by unauthorized users than in work-from-office or on-premise environments.
So, what happens when out-of-sight devices are being used by people other than your authorized employees?
Let’s look at three device sharing scenarios to understand why leveling up security for your endpoints by adding continuous authentication is so important to truly keep remote endpoint devices out of harm’s way.
Scenario 1 – “Innocent” device sharing
Working from home blurs the lines between work and life — both physically and technically. Devices that were previously dedicated to handling customer information and drafting business reports are increasingly being used by multiple family members, roommates, and friends for personal tasks like entertainment, education, and social networking.
But, when family members get access to an employee’s work computer, the employee no longer has full control and oversight over what is uploaded, downloaded, or modified on the company computer. When you consider the added risks of browsing insecure sites, clicking malicious links in personal emails, or following suspicious links on social media, it’s easy to see how these risks can quickly spiral out of control and threaten data security that lives on company endpoints.
Scenario 2 – “Foolish” device sharing

Imagine a worst-case scenario: your employee is working from a cafe, and their computer has a big sticker with your company’s name on it — basically letting everyone know that their device is potentially filled with valuable private information. Thinking it will be just for a second, they go to order another coffee and leave their company device unlocked on the table. While the employee isn’t looking, their device is stolen and the thief can now download and use any data to which your employee had access. The time it takes for the employee to gather the courage to let your company know that the device was stolen is more than enough for the damage to be done.
Let’s say that stolen laptop stored customer payment information. By having that data breached you would violate the Payment and Card Industry Data Security Standard (PCI DSS), which could lead to significant fines and damaged reputation for your company — especially if your security team could have taken precautionary steps to prevent this unlocked/unattended laptop from being accessed by an unauthorized user.
Read this whitepaper to learn how to stay compliant with PCI DSS when employees work remotely, and why continuous authentication of endpoint devices is a crucial step in complying with PCI DSS security requirements.
Scenario 3 – “Malicious” device sharing … (a.k.a fraud)
Usually done for financial gain, “malicious” device sharing occurs when employees intentionally share their work devices with unauthorized users, such as your company’s competitors, hackers, or other external parties. This is the most straightforward scenario because it implicitly involves a hostile actor wanting to access or steal confidential information such as internal company reports, proprietary information, or customer data. But in this case, your employee is actually voluntarily sharing the company device to help a bad actor perform the hostile act.
How ActiveLock bridges the security gap missed by Windows Defender for Endpoint?
For all the scenarios mentioned above, ActiveLock Continuous Endpoint Authentication (CEA) would act as a first line of defense to prevent the device from being shared or accessed by anyone other than the authorized employee. ActiveLock also works well in parallel with your antimalware systems — be it Windows Defender for Endpoint, or its competitors to give you greater control of your security architecture.
Simply put, ActiveLock limits endpoint access to one authorized user per device — effectively mitigating company endpoints from being shared. It works by continuously authenticating employees based on how they type. This way, even if the employee’s login credentials are compromised, or the device is left unlocked and unattended, access to crucial information is denied by applying a second, continuous layer of endpoint authentication that blocks any typing pattern that doesn’t match the owner of the device.
Get your complimentary ActiveLock license and see for yourself how Continuous Endpoint Authentication defends your endpoints in remote workforce environments.