Over the last couple of decades, multi-factor authentication (MFA) has become a popular term in the cybersecurity industry. Whether to protect an email account, log into a service, or perform a bank transaction, most of us have dealt with multi-factor authentication, an authentication mechanism where a user is only granted access to a system by sharing at least two pieces of evidence (e.g., a regular password you create and a one-time code sent to your phone).
This blog post is a review of the history of multi-factor authentication and how the evolution of MFA methods has changed the face of cybersecurity. Technological developments promise affordable, user-friendly multi-factor authentication methods, which include typing biometrics, an innovative approach to authentication which recognizes people by the way they type.
The context for authentication
Cybercrime is on the rise
In the early 2000s, Bill Gates predicted the death of the password as a single measure of account protection. In short, he was right.
Passwords are simply not enough. In recent years, billions of people have become the victims of cybercriminals who stole their credentials from the databases of corporations such as Marriott, Equifax, and Yahoo. Although hacked personal data is problematic to everyone, the bad news is that as long as there is a financial gain, hackers are not going to stop anytime soon. Instead, cybercrime is on the rise and continuously evolving. In fact, the forecast for annual global costs associated with data breaches is estimated to hit a staggering $6 trillion by 2021.
In fact, according to the Consumer Sentinel Network Data Book 2019, the top three types of identity fraud are credit card fraud, loan and lease fraud, and phone and utilities fraud. The report shows that the overall number of identity theft attacks has more than tripled between 2015 and 2019.
FinancesOnline’s article 16 Latest Cybercrime Trends & Predictions for 2020/2021 and Beyond indicates that:
- about 58% of companies are leaving 100,000 folders open to every employee
- about 56 percent of mobile users received and tapped on a phishing URL
- in 2017, the percentage of successful social engineering attacks rose to 79 percent
- 97 percent of data breaches attacks involve social engineering, while only three percent involve malware
Nonetheless, the risk of identity theft, account takeover, massive data breaches, and even of more sophisticated cyber threats such as social engineering, can be drastically reduced when multi-factor user authentication is introduced to the equation.
Authentication changed cybersecurity
The good news is more and more companies, institutions, and organizations are making multi-factor authentication solutions available. We should take advantage of this whenever possible, as applying MFA makes it much harder for hackers to access our private data.
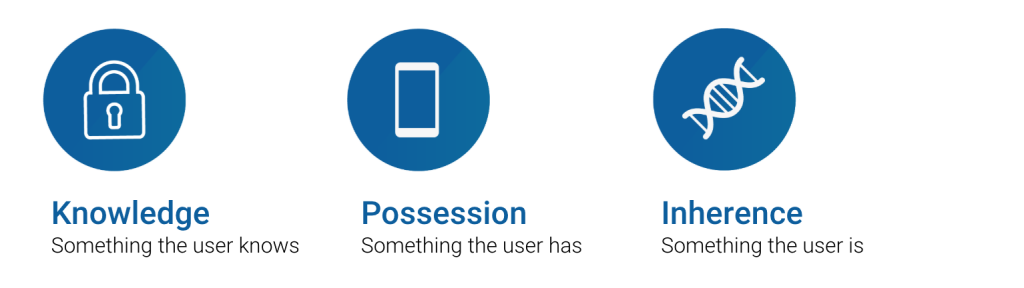
By requiring the provision of identity evidence, MFA ensures only the owner of an account can access it. Very simply, MFA entails the use of two or more security factors, including knowledge (something you know), possession (something you have), and inherence (something you are).
The history of authentication
Passwords are the oldest single-factor authentication system in the world. They’ve been used with computing systems since 1961 when the first computer system implemented password login.
Kim Dotcom claims to have invented two-factor authentication back in 1997 when he was awarded a patent for his “method for authorizing in data transmission systems employing a transaction authorization number or a comparable password.” However, AT&T’s patent precedes Kim’s, having been granted a couple of years earlier in 1995.
Regardless of who invented MFA, authentication is becoming more and more popular and affordable. In an age of data breaches, people should be given the opportunity to use it in order to secure their accounts.
Two reasons to avoid MFA
When authentication emerged decades ago, it was unappealing to the masses in large part for reasons that are still relevant today. For example, enacting MFA can be difficult due to the cost and inconvenience of adding additional hardware to the mix, such as portable tokens or biometric scanners. On top of that, the end-user is burdened with friction during the login process due to the effort required to memorize information or access tokens or having their biometrics scanned.
However, the evolution of authentication methods changed the face of cybersecurity
The evolution of multi-factor authentication
For a long time, MFA providers dwelled over security and usability ineffectively. While private individuals rejected MFA due to friction concerns, enterprises overlooked MFA due to complexity and costs associated with the procurement of software and hardware, on-premises deployment, and maintenance.
The ubiquity of smartphones pushed MFA adoption
However, the introduction and mass adoption of smartphones has reduced hassles users may experience during authentication.
Being able to produce both possession and biometric factors from one place (i.e., the user’s phone) brought an important decrease in disruption levels to users. Mobile phones support measures like one-time passwords (OTP) through SMS or email and key push notifications.
What’s more, Acuity predicts that by 2020, 4.8 billion smartphones will support biometrics such as fingerprint scan, voice recognition, or facial identification.
2FA gets worldwide attention
Moreover, cloud technologies, enterprise mobility, and the increased use of bring-your-own-device (BYOD) policies solidified the positive trend in MFA implementation.
Learn more about the best 2FA solution trends in 2021.
MFA got worldwide attention when large brands like Apple, Facebook, and eBay began adopting two-factor authentication (2FA) more frequently. Two-factor authentication requires a user to present two different types of identity evidence before being allowed to access an account.
For example, 2FA can include the use of a username and password (a knowledge-based factor) followed by one-time passwords via email or SMS (a possession-based factor) or biometric factors like a unique typing pattern.
Legislation and regulations, including PCI-DSS, PSD2, and NIST, align on requiring better protection for customer data against illegitimate access. They cover policies, procedures, and what organizations need to do to implement the authentication measures. These regulations apply not only to government agencies but also enterprises within a range of industries such as commercial security, finance, banking, software services, and healthcare.
The boost in MFA’s popularity happened when technological advancements and legislation were leveraged for global cybersecurity purposes.
MFA today
MFA has indeed become a popular phrase in the cybersecurity industry due to its widespread global use. A study by Okta, for example, revealed that, in 2018, 70% of companies used two to four different authentication factors to secure their systems. Turning on MFA is common as well, with 26% of individuals using it in their private lives and 38% at work.
MFA can easily be applied in many different use cases, such as account login, ATM authentication, online banking, driver’s license testing, and eLearning.
Today, three categories of factors are available to link an individual with established credentials:
Something You Know – Knowledge
A quick look at authentication factors is enough to help you understand the drawbacks of single methods of authentication. To many, these lower assurance factors are no longer perceived as trustworthy, particularly on their own. For example, security codes sent through text messages can be intercepted or redirected, and the answers to security questions are easily available via public records, on social media, or even by guessing.
Something You Have – Possession
There is a shift toward more secure factors such as one-time password codes (OTP), push notifications, app-generated codes, security tokens, smart cards, and physical keys. However, these can be stolen or lost, and they implicitly create additional costs and disruption.
Something You are – Inherence
Biometrics can be traced back to the 19th century. But it’s gained popularity in the digital era due to technological progress in the field. While finally taking off in the consumer space, the intrusive nature of biometrics remains a crucial reason for skepticism. Moreover, some biometrics—like fingerprints and facial scans—are less secure because they can be duplicated. Others like voice recognition are often too cumbersome. Taken together, all of these things stand as challenges for the user adoption of MFA.
The future of authentication
Behavioral biometrics
The trend in user authentication is behavioral biometrics, which analyzes patterns in the mannerisms of people (e.g., gestures, keystrokes, mouse movements, and gait). Sophisticated technology allows for a thorough comprehension of people’s unique actions. Behavioral biometrics is usually regarded as a supplement to traditional authentication approaches like passwords, smart cards, and PINs.
Typing biometrics used for secure and frictionless MFA
Update 2021: TypingDNA has launched a better MFA/2FA solution. TypigDNA Verify 2FA – replace SMS 2FA codes with better UX: Just type 4 words! Take a look here.
As mentioned, user-friendliness and privacy protection are critical in how people perceive authentication. Typing biometrics provides accurate online security based on how people type on their keyboards. The innovative approach to authentication analyzes new typing patterns against previously recorded samples to produce a matching score. If this score is within the predetermined threshold, the user can access their account.
With typing biometrics, people can stay secure while simply typing their credentials as they normally would. Even if credentials are stolen, security stays intact since it is almost impossible to replicate someone’s typing pattern.
Typing biometrics as an authentication method can be used to safeguard data, seamlessly in the background, on any keyboard, and without requiring additional hardware.
The evolution of multi-factor authentication changed the face of cybersecurity. Technological developments promise affordable, user-friendly multi-factor authentication, which is the main vector in any comprehensive privacy protection system. Typing biometrics is an innovative behavioral biometrics authentication method which focuses on individuals’ unique typing patterns, and which can be used as part of an integrated and robust MFA system. To learn more about how you can use the modern solution to identity verification to secure your systems, check this out.

