Enterprises can protect their sensitive information, customers, and employees from common types of social engineering attacks using behavioral biometrics for 2FA and continuous authentication. Behavioral biometrics verifies the identity of customers and business teams, preventing unauthorized users’ access to accounts and devices.
In this article, we’ll look into social engineering attacks and how they work and explore how to respond to growing cyber threats by focusing on achieving security with behavioral biometrics.

Securing the weak link of social engineering: the human element
In 2022, human error was the primary cause of 82% of data breaches. And, though training employees might look like the first obvious thing to do, having the proper security tools is equally important because it gives control over data, networks, and systems.
Here are a few tips:
- Include a social engineering penetration test or pen test to verify system weaknesses and identify employee improvement points by testing their susceptibility to social engineering methods.
- Have a Security Information and Event Management (SIEM) solution to govern your organization’s entire infrastructure and emit alerts based on analyzing log files from devices, servers, and applications.
- Have an Identity and Access Management (IAM) solution to categorize, authenticate, and offer authorization to your users depending on their privilege.
- Add behavioral biometrics to the mix as a user-friendly and innovative solution to verify your customers’ identities and set up a zero-trust strategy for your workforce.
How do types of social engineering attacks affect businesses and their customers?
Most types of social engineering attacks can target both individual persons and businesses. Baiting attacks tend to target corporate workers by manipulating them to plug an unknown USB drive into their work device. Phishing, on the other hand, tricks both customers and employees into disclosing confidential information or installing malware.
Whether you are an employee working for a corporation or a private person with online accounts, nowadays, businesses and individuals don’t have a choice but to stay up-to-date with new tactics as social engineering attacks constantly evolve.
What customers and employees can do to protect against social engineering?
- Be suspicious of unsolicited communications, like emails, phone calls, or messages from individuals or organizations that you don’t recognize. Most importantly, don’t provide personal or corporate information unless you know your recipient.
- Turn on all security features. Use strong and unique passwords. Passwords like “12345678” or “qwerty” will not suffice. And, because both organizations and customers have a role to play in securing access, for organizations, it’s important to prioritize turning on 2FA for all employee-used apps and accounts connecting to the corporate network, while customers should utilize 2FA whenever possible.
- Report suspicious activity whenever possible, even if it means submitting a report to your email provider. For businesses, inform employees and ensure they have easy-to-follow reporting procedures.

Social engineering hits companies where it hurts, with costs spiraling and the possibility of facing legal action and fines. In response to a phishing incident, organizations must proactively mitigate damage and bring in security specialists to manage the fallout. The worst part, however, is the loss of customer trust and permanent damage to the brand’s image – a long-term impact that must be addressed.
The situation is much more personal when customers are direct targets. In fact, 52% of victims feel highly distressed following an identity theft incident.
Quote: “Average organization targeted by over 700 social engineering attacks each year”. Source
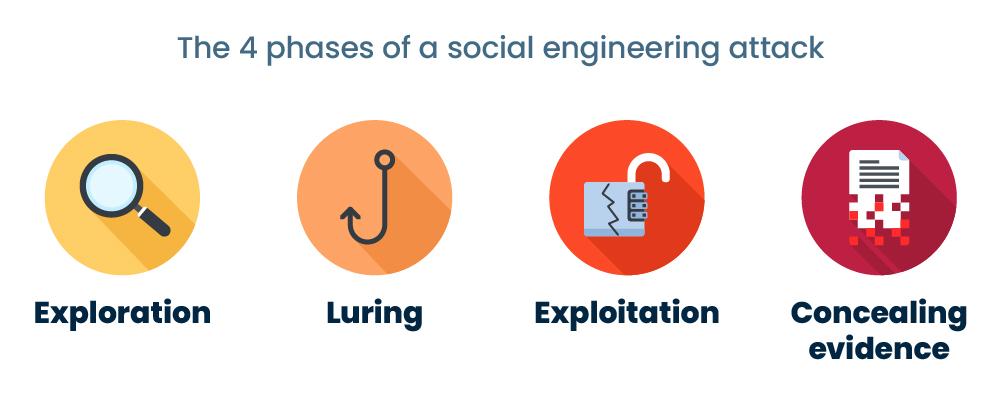
Understanding the 4 phases of a social engineering attack
Attackers usually undergo several phases of deception and manipulation, using all the tricks under their sleeves to study their target meticulously. So what are the stages of social engineering attacks, and what techniques do attackers use? There are many ways to categorize each step, but essentially, an attack would look like this:
- Exploration – Collecting information about the target through various methods. Online searches, social media, and posing as someone else when data gathering are just some examples.
- Luring – Using tactics such as phishing emails, baiting, or scareware to lure people into revealing or taking actions that lead to revealing sensitive information.
- Exploitation – Exploiting the information or access obtained from the target in the previous step & successfully achieving unauthorized access to the victim’s personal or business systems and data.
- Concealing evidence – As any skilled thief would do, cybercriminals would clear off their tracks by deactivating or destroying their digital and physical footprint and encrypting files.
Social engineering attacks are well-planned and sophisticated. But, understanding their phases can help individuals and organizations be better equipped.
Common types of social engineering attacks to watch out for: phishing and smishing
Phishing

Most of us were at some point at least targets of phishing, if not victims. This type of social engineering attack occurs when cybercriminals trick their targets into opening an email and clicking on a link that leads to a phishing website.
The origins of phishing may be found in America Online (AOL) in the 1990s when a group of hackers known as the warez community impersonated AOL workers to steal login passwords and personal data from AOL customers. According to rumors, the term “fishing” served as the basis for the phrase “phishing,” as the tactic entails “fishing” for sensitive data among a large user base.
Let’s exemplify phishing from a business perspective. Take an employee who receives an email from what appears to be a trusted company notifying them that there has been suspicious activity on their business account and that they need to update their personal information. When the employee hits the link, they reach a false website closely resembling the original. The employee enters their login credentials, which the attacker then captures and uses to achieve their goals.
Quote: “An October 2022 study analyzed billions of link-based URLs, attachments, and natural language messages in email, mobile, and browser channels over six months and found more than 255 million attacks.” Source
Smishing
Picture this scenario: you receive a text from your “bank” about your account balance. You click the link and add your credentials, and nothing happens. You’ve just been smished. Smishing is a type of phishing in which the attacker sends a text message containing a fake link. When people enter their credentials using the malicious link, they open the door to their personal information. Smishing differs from traditional phishing simply because it uses text messages as an attack channel rather than emails.
Other types of social engineering attacks businesses should consider:
Baiting
A common tactic attackers use is leaving a tempting item, like a USB drive or CD, in a public place packed with malicious content. When an unsuspecting person picks it up and inserts it into their device, or worse, into their corporate laptop, harmful things like malware installation or security breaches can occur. For example, a “confidential” labeled USB drive could sit temptingly on a coffee table in your office building. What would you do? What would your colleagues do?
Scareware
Attackers may present a fake virus warning or security alert, using fear to manipulate employees into downloading malware. For example, an employee may receive a pop-up warning on their computer screen about a virus and be urged to download malicious antivirus software.
Vishing/voice phishing
Attackers pose as trusted entities and ask employees for sensitive information over the phone. It’s like phishing or smishing, but via phone calls.
Why are passwords not enough, and how can 2FA and continuous authentication help?
We all know passwords are the first line of defense when securing our accounts. But did you know that 81% of all data breaches occur due to weak, reused, or stolen passwords? That’s why passwords alone are not enough to keep our information safe and why two-factor authentication (2FA) and continuous authentication come in handy as added security.

2FA is a security method that requires two identity verification forms. There are three types of authentication methods, and any combination of those types can create 2FA or MFA (multi-factor authentication): something the user knows (like a password), something the user has (like an SMS code or security key), or something the user is (biometrics).
By adding two or more of these extra layers of security, we can prevent unauthorized access to sensitive information. So, even if a password is compromised, 2FA will make the hacker’s job a lot harder.
For customers, 2FA could mean a one-time code sent to their phone or a fingerprint scan. This additional step helps to ensure that their personal and financial information remains safe whenever they log in to an account or perform an online transaction.
For employees, 2FA helps prevent corporate data breaches and other security incidents that could compromise sensitive information and harm the business’s reputation. Companies must require employees to use 2FA when logging into corporate endpoints or accounts.
Beware of phishing or smishing links that might provide fake OTPs (one-time passcodes), and be vigilant when required to provide OTPs over the phone. As you know, the person on the other end might be an impostor, only pretending to be a representative of your bank or a trusted company. To stay safe, never share OTPs. If you’re looking for an alternative 2FA solution that doesn’t require the use of mobile phones, learn here why behavioral biometrics is a more user-friendly alternative than traditional 2FA, like OTPs.
Continuous authentication goes further than 2FA and monitors the user in real-time to flag suspicious behavior, even after they were successfully authenticated at login. Continuous authentication works with behavioral biometrics such as typing patterns, mouse movement, device orientation, time of day, and other characteristics to verify if the user is the trusted account owner.
How to prevent common types of social engineering attacks with behavioral biometrics
By identifying user behavior irregularities that indicate unauthorized access, behavioral biometrics enhance the security provided by 2FA and continuous authentication solutions.
Just like with any other technology in cybersecurity, it’s not a good idea to rely solely on behavioral biometrics, so use a combination of measures whenever possible. Along with firewalls, antivirus software, strong passwords, and authentication, remember to promote security-conscious behavior within your departments. Discover how to use behavioral biometrics to enhance your business security.

How TypingDNA prevents common types of social engineering attacks with typing biometrics
TypingDNA provides behavioral biometrics technology based on how people type, called typing biometrics. By analyzing the unique typing patterns of users, typing biometrics can accurately verify users’ identities and be deployed in more complex 2FA and continuous authentication solutions.
Learn more about TypingDNA typing biometrics for 2FA and continuous authentication.

