The massive increase in the number and sheer size of data breaches along with the advancement of automation technologies have made credential stuffing a popular attack vector, among others, such as malware, viruses, phishing, and social engineering.
This blog post reviews two quick ways on how to use keystroke dynamics authentication to prevent credential stuffing and secure your customers’ information in a user-friendly way.
What is credential stuffing?
Credential stuffing is a form of cyberattack in which a list of credentials obtained from a data spill becomes available for sale or free download. Once acquired, malicious actors use them through automated login flows to try and gain access to many different services in an attempt to breach accounts, make unauthorized transactions, and even steal personal information.
The name credential stuffing comes from the large-scale testing (i.e., stuffing) of mass-stolen credentials (i.e., usernames and passwords), usually on top-rated popular services such as social media platforms, food delivery services, and transportation apps.
The most dangerous part of credential hacking is what happens after a successful account breach. Once the hacker gains access, they can obtain personally identifiable information—such as credit card numbers or answers to security questions.
Such valuable data can then be used for direct transactions through the compromised service. It can also be retained for future use in more complex cyberattacks, such as phishing.
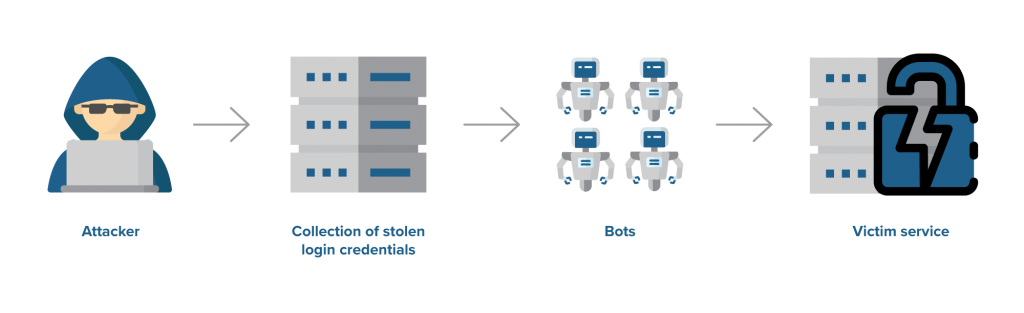
Credential stuffing vs. data breach: Spot the vulnerability
The main difference between credential stuffing and a standard cyberattack has to do with where the vulnerability stems from.
With credential stuffing, hackers gain unauthorized access to a person’s account through their legitimate username and password, which were discovered in credential dumps previously acquired from publicly available information that was unintentionally disclosed.
Credential stuffing is different from other cyberattacks in the sense that it does not rely on brute force, unlike common breaches of internal systems. It also doesn’t rely on password guessing or more complex identity fraud attempts like social engineering and phishing.
Instead, credential stuffing primarily has to do with the poor choices people make with regards to account security. For example, they might reuse the same passwords across a multitude of channels, and they might not opt to take advantage of additional security layers such as a one-time passcode or behavioral-based authentication—if those options even exist in the first place.
In fact, in a recent survey, Google found that 51% of respondents use the same password for most of their accounts. Simultaneously, one-third of respondents didn’t know whether or not they have turned on two-factor authentication (2FA). Moreover, the 2018 Verizon Data Breach Incident Report estimates that 81% of hacking-related incidents are due to compromised passwords.
Why is credential stuffing profitable?
The success rate of credential stuffing attacks can be as low as 0.1%. However, hackers can quickly test the increasing number of leaked information collections as well as the significant number of credentials these collections contain by enlisting the help of bots.
Bots can steal username-password pairs and fire off these combinations to a range of websites, which in turn will communicate back whether the logins were successful. Hence, a million of credentials tested imply a yield of 1,000 successfully cracked accounts.
To give you a better grasp of the magnitude of credential stuffing attacks, imagine what would have happened if hackers had used the information acquired from Sony’s PlayStation Network (PSN) enormous 2011 data breach, which affected over 77 million PSN users. The leaked details included names, addresses, login credentials, IDs, and handles but also other sensitive information, such as billing addresses and security questions.
If the breach happened today, with hackers’ increased ability to use automation to boost their attacks, and based on the estimation that only 0.1% of credential stuffing attacks are successful, the PSN data breach would have allowed hackers to gain unauthorized access to roughly 77,000 accounts. Depending on the types of services they would have automated the login flows for, hackers would have been able to access users’ accounts with their legitimate usernames and passwords, exploiting them the same way the owner would.

If your password is in the list below, change it now
A survey from the UK’s National Cyber Security Centre (NCSC) revealed that the most commonly hacked passwords were as follows:
- 123456
- 123456789
- qwerty
- password
- 111111
- 12345678
- abc123
- 1234567
- password1
- 12345
Two quick ways to prevent credential stuffing
Companies can keep their customers safe from fraudulent activities—like password reuse and bot traffic—on their publicly facing websites and apps by deploying two-factor authentication, or adaptive authentication aka risk-based authentication.
What follows is a quick overview of what these types of authentication are and how TypingDNA’s typing biometrics technology can be deployed to maximize security while maintaining a stellar user experience.
The way you type your password can keep you safe
Relying on passwords alone is rapidly becoming a thing of the past. At the same time, two-factor authentication is becoming increasingly familiar by the day, as many large brands such as Google, Apple, and Amazon offer their customers 2FA security.
Simply put, 2FA adds an extra layer of security to ensure that a person is who they claim to be online. A well-known authentication combination is the use of passwords alongside a six-digit passcode received via SMS.
Essentially, the harder it is for a hacker to breach a certain authentication method, the more secure your information is. Knowledge or possession factors like passwords, one-time passwords (OTPs), or tokens weaken security and can be easily breached. Even physical biometrics like fingerprints can be spoofed.
However, behavioral biometrics provides an additional security barrier, which is almost impossible for someone to get around, as it is embedded in the unique way each person interacts with a device. As such, behavioral biometrics is one of the most reliable methods of two-factor authentication.
Also known as keystroke dynamics, typing biometrics can be used to prevent credential stuffing attacks. Typing biometrics 2FA is frictionless, too, happening in the background during the sign-up and login processes. It analyzes a user’s typing pattern, which is then matched against previous enrollments to verify someone’s identity. It merely requires an existing keyboard, and no additional hardware or maintenance costs. Check out this quick guide on choosing the right authentication measures for your company’s needs.
Adaptive authentication (risk-based authentication)
Trying to keep the level of sophistication high during credential stuffing, attackers tend to use a variety of computers and IP addresses to mask the attack while continually trying to get onto a website or app with the stolen credentials.
Such measures can be used against attacks through adaptive authentication, also known as risk-based authentication (RBA). To trust a user, an RBA system would look at several characteristics, including the user’s IP address, location, and behavioral biometrics.
Not all user actions carry the same risk. As such, the trust level earned by the user through multiple authentication modalities must match the risk of the desired activity in the platform. When a riskier situation is flagged, the RBA system will prompt the user to introduce additional proof of identity to allow the action to continue.
For example, when users log in with passwords or by typing generated words, TypingDNA can provide a risk score based on the way they type, establishing a reliable trust level. Then, based on that trust level, an RBA system can be used to escalate or de-escalate the authentication process.
Where to start?
Try the demo to see how typing biometrics authentication can protect your account based on the way you type. For more information, contact us, and we’ll be happy to help you get up and running.

