With cyber breaches making headlines seemingly every week, one thing is clear — passwords alone are no longer enough to keep us safe. While stopping all online crime is not a realistic goal, Multi Factor Authentication (MFA) is a simple but critical step in your security flow that can massively reduce the likelihood you or your users will be the next victim.
In this article, we’ll cover in detail what Multi Factor Authentication is, and the huge difference it makes in protecting online accounts.
First, let’s define MFA and explore why it is so effective as a security strategy.
Table of contents:
- What is Multi Factor Authentication (MFA)?
- What Are the Main Types of Multi Factor Authentication?
- When To Require Multi Factor Authentication?
- What’s the Difference Between MFA and 2FA?
- Is Single Factor Authentication Safe?
- Things to consider when rolling out your MFA strategy
- How to choose the right MFA: You’ll need to focuse on user-experience
What is Multi Factor Authentication (MFA)?
Think of Multi Factor Authentication (MFA) as a layered defense around your online account. Instead of relying on a single piece of evidence like a password to prove who you are, MFA requires multiple methods or “factors” of verification to grant access.
MFA requires that digital users provide at least 2 pieces of proof to verify their identity. Each piece of evidence must come from a different category: something they know, something they have, or something they are. Even if one of the factors is hacked, the chances of another factor also getting compromised are pretty low.
What Are the Main Types of Multi Factor Authentication (MFA)? Knowledge, Possession, Inherence
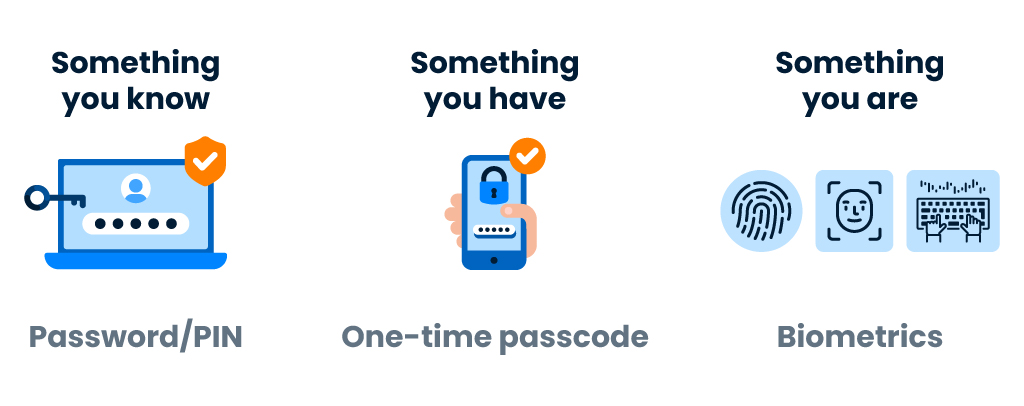
Knowledge (“something you know”)
- This method involves questions which only you know and can answer when required, such as a username and password, a PIN, or a security question.
Possession (“something you have”)
- This method refers to something you physically have in your possession like a mobile phone, security token, or one-time password (OTP) sent through SMS or email.
Inherence (“something you are”)
- This method uses something that is inherent to who you are as a human, like a physical biometric such as a fingerprint, face, handprint, retina, and behavioral biometrics such as voice recognition, or typing patterns.
Multi factor authentication involves at least two of these categories, or all three.
Because basic personal information such as passwords can often be stolen through research, phishing and social engineering, it isn’t a strong method of authentication on its own. But, when you combine this semi-weak piece of knowledge with an additional piece of evidence, you make it much more difficult for a hacker to break in.
Why do I need Multi Factor Authentication (MFA)?
Though passwords may be the most common way to authenticate your online identity, they increasingly provide very little protection. Unfortunately users often make it even easier for hackers by choosing weak passwords, reusing the same password across multiple applications, storing passwords in insecure locations and keeping the same password for long periods of time. In fact more than 80% of people ages 18 and up reuse the same password across multiple accounts. These practices may help them remember their logins, but this behavior is the equivalent of inviting hackers in through the front door.
Once a password is stolen, hackers can use those credentials to log into applications and business systems, bypass other access controls, and do serious damage.
By creating additional layers of security around your online account, multi factor authentication makes it harder for bad guys to log in. So even if they steal your username and password, they’ll be stuck because they don’t have this extra piece of evidence to prove that they are you.
Companies are recognizing these risks and stepping up. More than 55 percent of enterprises use multi factor authentication to protect security — and that number rises each year.
When To Require Multi Factor Authentication (MFA)?
MFA is quickly becoming a requirement for customer applications, but it can add friction. Unlike your employees, your customers have a choice about working with you, and can easily abandon you for a competitor. To make MFA attractive for customers, you must find the right balance between security and convenience.
This balance between security and convenience is key. If you add too much friction, your users will become frustrated and potentially churn — leaving you for a company that offers a more convenient digital experience. But if you don’t add enough friction, then you leave your brand and your user-base exposed to unnecessary risks, data leaks, and cyber breaches.
Though MFA is critical to securing online accounts, some organizations may not feel the need to require multi factor authentication in all cases, particularly if the user experience becomes too cumbersome.
To get customer MFA right, you need to make implementation choices that ensure both customer experience and security are optimized for various use cases. You also need to determine the best way to introduce multi factor authentication to your customer base and decide if that means requiring it or making it optional.
To optimize employee and customer convenience, you might choose to bypass MFA in low-risk scenarios, while requiring stronger security in high-risk situations — particularly for sensitive data or high-value transactions.
For example, if an authenticated user is just trying to view their “deals of the day” on a retail app, chances are you won’t need multi factor authentication in this scenario. But if they’re trying to update their email address or billing preferences, and they’re using a device they haven’t previously used, you may want to add MFA and introduce a little friction to their experience to be on the safe side of security.
What’s the Difference Between MFA and 2FA?
Multi Factor Authentication (MFA) requires two or more factors of authentication. Two-Factor Authentication (2FA) requires exactly two factors of authentication. Think about it this way: every Two Factor Authentication is a Multi Factor Authentication, but not every Multi Factor Authentication is a Two Factor Authentication.
It’s also very important that the factors be different kinds of factors. Having two passwords, or a password and a memorized PIN, is just two of the same kind of factor – things you know – and if somebody compromises one password, they could compromise both. It should be a combination of at least two of the three different kinds of factors to be secure. Crooks may steal your password, but they can’t easily steal your fingerprint.
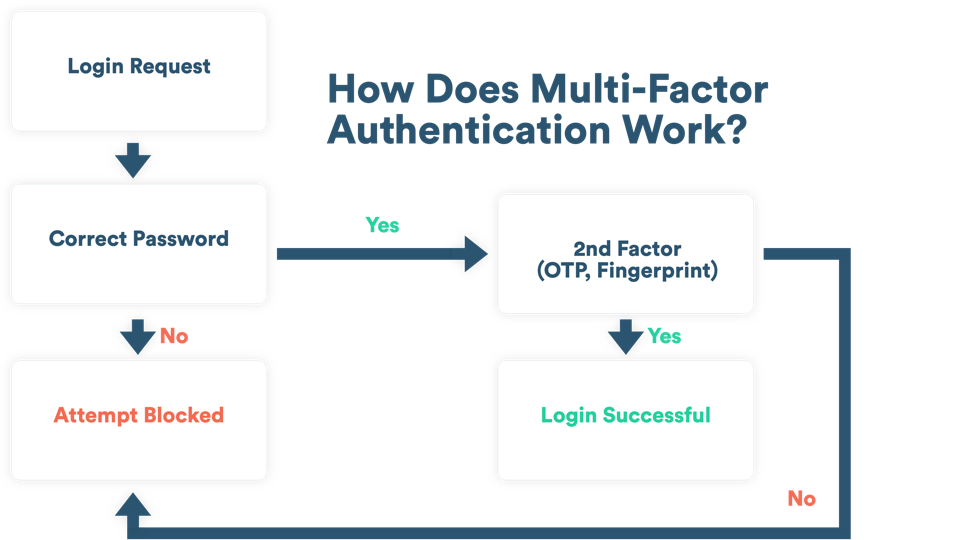
Is Single Factor Authentication Safe?
Passwords are not enough. We all have more passwords to keep track of than ever before. So most users create passwords that are easy to remember, and therefore weak. People tend to reuse those same passwords across multiple websites at alarming rates. Hackers prey upon this vulnerability every day.
There’s lots of challenges associated with single-factor authentication. The bad guys are very good at getting their hands on your password. Three of the most common methods are:
- Phishing Emails: one wrong click on a link and you’ve just compromised your entire system. Hackers are fantastic at pretending to be someone they’re not. One day you’ll receive an email that looks like it’s from a company or a person whom you trust. But once you click on the link, you’re taken to a fake site that appears to be legitimate — asking you to enter your username and password to log in. But what you don’t know is you’ve just entered your credentials on a fake website, and hackers now have your sensitive information.
- Credential Stuffing: to make matters worse, because so many people reuse the same username/password combinations across multiple websites, this creates a domino effect where hackers may try those same username and password combinations on other sites in an attack called credential stuffing.
- Brute Force Attacks: hackers also like to use another popular attack method called brute force attacks to gain entry into accounts. This is more of a trial-and-error method used to guess a user’s password. Hackers get their hands on a list of valid usernames from a website, then use a bot to attempt to “force” a login using a list of popular weak passwords.
The Cybersecurity and Infrastructure Security Agency (CISA) — a U.S. federal agency under the Department of Homeland Security recently added the use of single-factor authentication to their Bad Practices list of exceptionally risky cybersecurity practices.
Multi factor authentication guards against account compromise by ensuring there is an extra level of security attached to every single log-in attempt. Even if your account password gets compromised, it’s highly unlikely that a cyber criminal will also possess your smartphone or fingerprint, and so MFA greatly improves account security.

Things to consider when rolling out your MFA strategy
Introducing your users to MFA is a delicate process: Customers may push back if they’re suddenly required to start using MFA — and unlike employees who have no choice but to follow the newly enforced security, customers may simply leave you for a competitor where the sign-in process is smoother (even if it’s less secure).
Without the right context, your customers and employees may feel that multi factor authentication is a hassle that slows them down instead of protecting their sensitive information. Get ahead of this mindset and raise your MFA adoption rate by explaining the importance of MFA before, during, and after you roll out your MFA strategy.
EDUCATE YOUR USERS:
Before rolling out the new MFA program, make sure that the users that will be impacted are alerted and prepared for the transition at least 2 weeks in advance. Alert users multiple times to make sure they’re aware of what’s coming. Make announcements through email and other mediums to make sure the message is received. Try to provide as much information as possible in the message without overwhelming them with too much information. Be sure to make it clear why MFA is important, and how it will protect their accounts and benefit them.
TRAIN YOUR TEAM:
IT leaders often forget that there are many who are still unfamiliar with MFA. People are less likely to adopt new procedures or follow through on new policies if they do not understand the reasoning behind it. Make it clear to your employees that changes in policies and procedures are necessary to stay up to date and remain protected from new threats.
They may be worried that this process change will take up time they feel could be better spent elsewhere. Explain how MFA protects both company information and employee’s personal data, and consider sharing other steps your company is taking to enhance privacy and security. Explain to your users how an account that relies solely on password protection is vulnerable to hacking, and briefly review the sophisticated attacks which are now common and what your company is doing to protect both workers and customers.
When your MFA program is rolled out for the first time, be sure to share all the training resources you have the day before. Don’t forget to prepare your IT team for an increase in tickets surrounding the new MFA adoption, and be sure they are ready to help with the most common questions.
DRIVE MFA ADOPTION WITH INCENTIVES OR REWARDS:
Not seeing enough people activating MFA or 2FA on their accounts? Consider incentivizing users with rewards. When Epic Games needed to secure their popular Fortnite game, they used a very clever tactic by rewarding gamers with exclusive in-game rewards and bonus features when they took the extra step to activate 2FA on their Epic Game accounts. Epic Games was happy because their platform was now more secure; gamers were thrilled because they were rewarded for their extra effort.
How to choose the right Multi Factor Authentication: You’ll need an MFA that’s focused on user-experience
The best modern MFA solutions find the right balance between security and convenience by supporting multiple authentication options, implementing adaptive policies and integrating seamlessly into existing applications.
For employees, even though adopting MFA is a requirement, a cumbersome authentication experience results in frustration, lost productivity, and increased calls to help desk — costing you money on all sides.
But for customers, enforcing MFA is even trickier, since they expect every interaction with you to be seamless. So if your log-ins are clunky, they’ll abandon the flow or even churn altogether and leave you for a competitor.
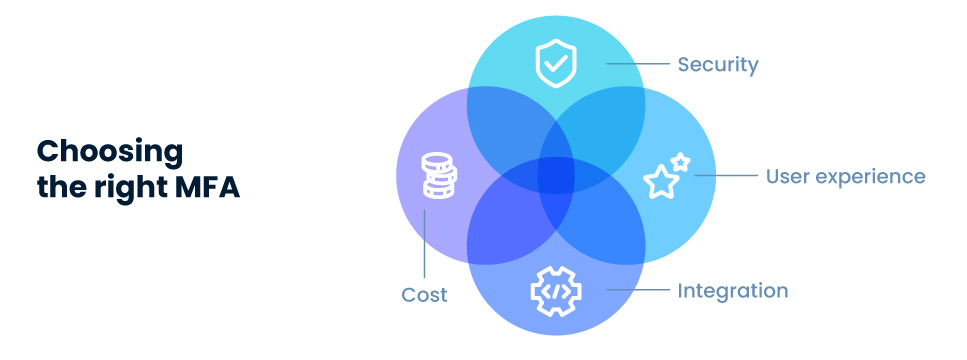
You must find an MFA solution that strikes the perfect balance of security and user experience to keep your customers happy and boost your MFA adoption rates. But you must also find a solution that’s easy to integrate for your developers, and one that delivers authentication at a great price.
Verify 2FA from TypingDNA is a smooth user-friendly authentication experience that’s easy to integrate, quick to rollout, and easily adoptable by your users. And the best part, your devs can integrate the full MFA solution in under 10 minutes. Learn more or try a live demo to see Verify 2FA for yourself.

