BYOD stands for Bring Your Own Device and is a practice in which personal devices are used to complete work-related tasks. BYOD has both pros and cons. On the one hand, BYOD can increase productivity and lower costs for enterprises and their employees. On the flip side, allowing contractors or employees to use their personal devices for work can lead to security vulnerabilities.
When allowing BYOD, organizations must always uphold the goal of achieving BYOD security to keep their data, networks, and systems safe from unnecessary cyber threats and unauthorized users.
Below, we explore why BYOD is growing in popularity and what steps enterprises can take to deal with BYOD security and protect enterprise data, applications, and systems. We also look at how deploying continuous endpoint authentication (CEA) on both BYOD and enterprise-owned devices prevents unauthorized users from taking over these devices.
Table of contents:
- What does BYOD mean?
- What is BYOD?
- Why is BYOD becoming more popular?
- BYOD advantages
- BYOD disadvantages
- What is BYOD security?
- Top 3 BYOD security risks & challenges to keep in mind
- Top 3 BYOD security best practices to aim for
- Why continuous endpoint authentication is necessary for BYOD security
- How ActiveLock Continuous Endpoint Authentication helps you achieve BYOD Security
What does BYOD mean?

BYOD is an acronym for Bring Your Own Device and is a rising global trend in which employees are allowed to do work-related tasks on their personal computers, laptops, tablets, or smartphones — instead of using a company-issued device to do their job.
Variations around this acronym have also appeared, including BYOPC (Bring Your Own Personal Computer), BYOT (Bring Your Own Technology), and BYOP (Bring Your Own Phone). However, BYOD is the most common and increasingly popular across many industries.
Before finding out why BYOD is rising in popularity, let’s take a closer look at what BYOD as a policy in the workplace implies. BYOD for enterprises can mean increased employee productivity and added value generated per employee.
A BYOD-carrying employee works an extra two hours daily, generating $350 worth of value each year for the enterprise.
BYOD practices are a great example of IT consumerization, which is how technologies traditionally oriented toward consumers can shape how enterprises approach work management.
To understand why BYOD is a consumerization trend, let’s look at the Gartner Glossary definition of consumerization which is “the specific impact that consumer-originated technologies can have on enterprises. […] Consumerization is not a strategy or something to be “adopted.””
In the following sections, we approach BYOD as a policy adopted by organizations and as a trend that takes place outside a clear framework developed by organizations.
What is BYOD?
In the workplace, BYOD policies allow employees to conveniently access corporate networks, systems, applications, and software from their own personal devices. Whether it’s a smartphone, a computer desktop or laptop, a tablet, or a USB device, any personal device can serve as BYOD.
For enterprises, BYOD can take multiple forms:
- Employees use their personal devices for work purposes through the corporation’s network, like answering emails, accessing cloud drives, having calls, or handling sensitive data and files.
- Employees use their personal devices for personal reasons during work hours through different internet carriers than the secured company-owned network and without connecting to the enterprise secure VPN.
For many enterprises, these two scenarios can also take place simultaneously —with or without the company’s knowledge— which brings us to the point that BYOD adoption cannot exist without clear policies to guard the company networks or proper endpoint security.
But before we see what a company’s BYOD policy should entail, let’s examine why BYOD became so popular.

Why is BYOD becoming more popular?
In the past, employees would solely use devices provided by the employer. But, as the global personal computers market continues to grow and as more and more people own gadgets, BYOD has become a highly convenient practice for employees and employers alike.
BYOD can mean greater flexibility for employees to take calls and deal with work issues anywhere and at any time. While for employers, BYOD can mean increased productivity and lower costs.
BYOD is very popular. As of 2022, BYOD is now standard practice for 83% of companies, and that is expected to go up.
Another reason BYOD is popular is that significantly more employees are working remotely, and juggling between two laptops or phones (one for work and one for personal use) can be highly inefficient. Employees generally choose convenience over security and use their personal devices to access sensitive corporate information and do their work tasks.
However, organizations should take the positive aspects of the BYOD trend with a grain of salt and stay alert to the security threats associated with BYOD, which we’ll look at below.
The BYOD security market is expected to reach $69 Billion by 2030 at a CAGR of 37%.
But, for now, let’s clarify the advantages and disadvantages of BYOD.
BYOD advantages
Productivity is the best word to encapsulate the advantages of BYOD. Not only are employees more comfortable and thus more productive when they work on their own familiar devices — but for any company, BYOD can also significantly cut device and software costs and the costs of maintaining and reassigning company devices.
In the U.S, the productivity gains weekly per employee rise to 81 minutes due to employees being more efficient and available to their colleagues and managers.
We are so used to having our cell phones close by at all times that it comes in (literally) handy to reply to an email while at a doctor’s appointment or to Slack a colleague when we are on vacation. For some, being so easy to reach by their manager or colleagues seems to improve work-life balance, while for others, it can make things worse.
61% of organizations expect employees to be available remotely, even if they don’t provide a company phone, while employee satisfaction with BYOD is at 70%.
BYOD disadvantages
While BYOD has many advantages, the risks and vulnerabilities that come with BYOD cannot be overlooked. Among many other corporate practices, the COVID-19 pandemic also significantly impacted the trend of BYOD adoption. According to a Palo Alto survey, 60% of companies have expanded BYOD to allow their employees to work remotely during the pandemic. However, there’s a bit of a tradeoff since the same study also noted that organizations implementing BYOD must deal with employees being 8 times more likely to circumvent security practices.
Another alarming statistic to note when discussing BYOD is that 17% of employees don’t even notify IT departments that they are using personal devices for work purposes.

Going through these advantages and disadvantages gives us a better understanding of why BYOD security is the centerpiece that holds BYOD adoption together for any company. So, let’s take a closer look at how to understand and achieve BYOD security.
What is BYOD security?
BYOD security consists of all organizational processes to prevent and navigate BYOD security risks and ensure that company-related data found on BYOD devices are protected against fraudulent activity and unauthorized users.
The three main aspects of BYOD security are network security, device security, and Identity and Access Management (IAM) practices.
BYOD and network security
BYOD devices brought to the workplace but not connected to the company network are much less problematic than devices employees use to conduct work through the company network. While the former requires BYOD policies (and enforcing those policies), in the latter case, IT departments also need to ensure no unnecessary vulnerabilities to the company systems emerge.
When enabling remote user access to enterprise resources, especially on BYOD devices, the two approaches to embrace are a traditional VPN-based access architecture and a zero trust architecture. While having multiple access layers secured with firewalls can help prevent outside breaches, a zero trust architecture implies giving no inherent trust from the network to the internal users. This can be achieved by authenticating each network connection and end user continuously. In a few sections below, we take a more in-depth look at why continuous endpoint authentication is necessary for BYOD security.
BYOD and device security
Securing BYOD devices can be a difficult task for any IT department and can stretch their resources too thin when many different devices, operating systems, and software versions exist in the same corporate environment.
So, before allowing employees to access company resources from anywhere, it’s best to set strict security protocols, such as requiring strong passwords and lock screens when phones go idle. Adopting two-step authentication whenever possible and implementing mobile device management software on BYOD devices are also highly recommended.
BYOD and IAM systems
Identity and Access Management (IAM) solutions are great for securing employees’ access to company resources and tools. IAM delivers more straightforward and centralized management of the workforce’s access to files and resources found on a company’s networks and systems.
With IAM systems, companies can restrict data access using the principle of least privilege on both BYOD and company-owned devices by only giving employees access to files and resources they actually need to do their particular job. IAM solutions also offer modern authentication methods, which can be combined with multifactor authentication solutions to take security to the next level.
Why is device security the key to BYOD security?
When you take into account the popularity of BYOD (bring your own device) and the growing use of IoT (internet of things) across physical devices, any corporation’s network security by default has to be able to serve thousands, if not tens of thousands, of devices and endpoints — and do so seamlessly.
This means network security can become harder and harder to manage as BYOD adoption expands throughout an organization. So, when approaching BYOD security, try viewing all BYOD devices as points of access that must be guarded at all times and at all costs. This includes your employees’ personal devices on which company networks are accessed, but it’s also relevant for company-owned devices and any other IoT devices that connect or communicate with corporate systems.
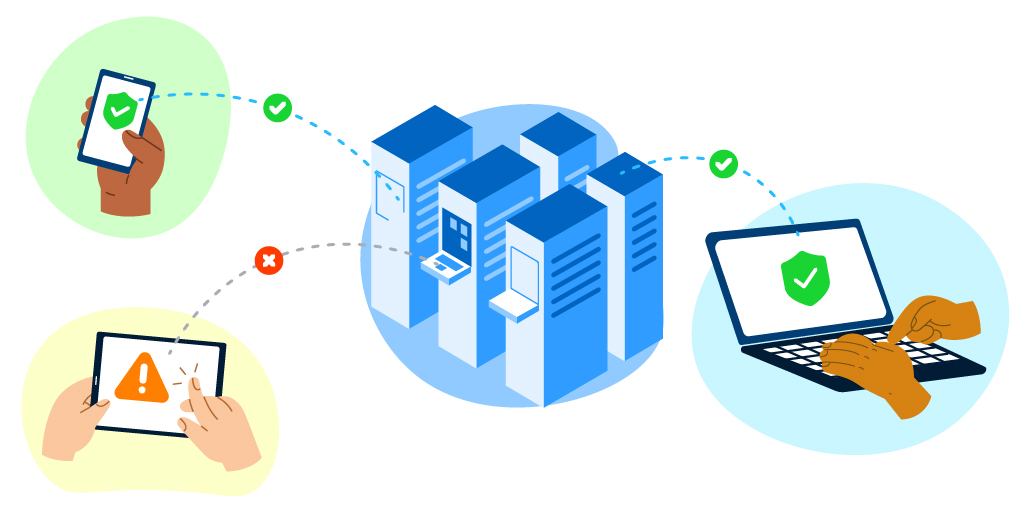
Top 3 BYOD security risks & challenges to keep in mind
1. Malware
Malware is even riskier when employees access a company network from their own devices. Whether at home or the office, malware from employee-owned devices can spread onto company systems through Trojans found in email attachments. It can also spread through cross-site scripting (XSS) found on the internet when hacker code is injected into web pages and downloaded onto the employee’s device or even via a random connection to an unknown WiFi network.
Though modern antivirus/antimalware software such as Windows Defender for Endpoint can prevent a cyberattack, they are largely unable to stop device sharing or prevent insider threats. Learn more about endpoint security and check out the Windows Defender security gaps regarding insider threats.
2. Devices being lost or stolen
The physical security risks of BYOD devices imply missing, forgotten, lost, or stolen devices as a classic entry point for malicious insiders. Once inside the device, a hacker can pretend to be the actual employee and start a series of actions that will end up damaging the company indefinitely or until the IT department can lock the device and remove its connection to the company network.
Yet, the true cost of a lost mobile or laptop device goes beyond the price of replacement. It has to do with all the other unapparent costs, such as productivity loss, support required from IT, and management time spent to get back on track.
In the event of misplaced or stolen devices, company data can be lost permanently or get in the wrong hands. So having a real-time backup solution installed on BYOD devices is another must-have.
70 million smartphones are lost yearly, with only 7% ever recovered.
One solution companies can deploy to prevent unauthorized access in case devices are lost or stolen is to deploy continuous endpoint authentication (CEA) on all devices — company-owned and BYOD. CEA on employee devices means the user’s identity is verified at all times, not just at login or once in a while throughout the day. CEA is non-stop, making it a great additional tool for safeguarding against increased BYOD adoption. We outline some more details about CEA below.
3. Unclear security protocols
Businesses that don’t invest enough time and effort in educating and training their workers on security procedures typically experience security breaches. Not only are there external security risks posed by unauthorized users gaining access to company networks, but there is also a risk associated with insider threats, such as employees “innocently” sharing their work devices with friends and family. Check out these insider threats to look out for with a remote workforce to learn more.
The simple requirement that new employees read a brochure describing security measures is not enough in today’s cybersecurity landscape. In 2017, a computer attack on a Bithumb employee’s home computer exposed the personal data of roughly 30,000 users of the South Korean cryptocurrency exchange Bithumb, according to Yonhap News. This event started a discussion about BYOD becoming a new workplace standard and the dangers of employees accessing sensitive information on personal devices.
Because of these threats, companies need to take strategic action, starting with defining a clear and sustainable BYOD security policy and ensuring the policy is known among employees, agreed to by both employees and contractors, and followed accordingly.
Top 3 BYOD security best practices to aim for
Have Mobile Application Management (MAM) or Mobile Device Management —or both— on BYOD devices
Mobile Application Management (MAM) are systems that give companies the ability to control what applications are being installed on any employee-owned device connected to the company network. In contrast, a more invasive approach is Mobile Device Management (MDM) which allows employers to access and control the BYOD device itself.
In truth, these options sound almost impossible to implement on employees’ personal devices. But, MAM seems to be a much easier “sell” to employees than MDM. This is because, in the case of application management systems, employers supply applications through a company portal. MAM will allow the company to restrict portal access to a company-provided VPN, effectively securing confidential information. While the bright side is that all work-related activity performed on a mobile device resides on the MAM portal, the downside is that all other user activity is not secure, as — by design, MAM systems cannot monitor or control anything other than the company portal.
MDM systems, on the other end, can not only track the location of all BYOD devices regardless of who owns them, but they also give companies the ability to lock mobile devices remotely and even wipe all device data in case they get lost or stolen. However, remote wiping and general employer control on personal devices is a controversial topic for both employees and employers, as it opens the door to employee frustration and dissatisfaction.
Get Continuous Endpoint Authentication (CEA) on BYOD devices
CEA prevents unauthorized users from taking over these devices by continuously checking the user’s identity even once they’ve authenticated at the front door with their username and password. CEA is the key component of a Zero Trust model because it solves the issue of “what is happening between security checks or between logins.”
TypingDNA created ActiveLock, a privacy-focused continuous authentication app which keeps unauthorized users out of any endpoint. ActiveLock can also be easily installed on employees’ BYOD devices in a user-friendly way. Learn more about ActiveLock.
Educate your workforce about BYOD security
With human error being the number one reason for data breaches, educating employees about proper device safety is no longer something companies can avoid. Spotting malware-containing apps, sharing threat updates, and securing devices beyond the usual security settings are just some of the concerns to address when training BYOD employees.
According to Verizon’s 2022 Data Breaches Investigations Report, 82% of data breaches involved a human element.
Why continuous endpoint authentication is necessary for BYOD security
As more people work remotely and on personal devices, every company deals with the undeniable yet invisible vulnerability of who is the person behind out-of-sight endpoints: is it the employee, or is it an unauthorized user? This means that when devices are out of sight, you never actually know who is on the endpoint once they’ve logged in at the “front door” with their authentication credentials. Security teams can’t recognize when a breach happens unless a Continuous Endpoint Authentication (CEA) solution is running on company-owned and BYOD devices.
But, when you add CEA deployed across BYOD devices, you no longer need to worry about unauthorized users taking over remote endpoints without your knowledge.
With round-the-clock user activity monitoring and authentication, CEA gives companies insight into potential threats by flagging suspicious behavior, triggering an alert when an unauthorized user’s typing pattern is detected on the device, and even locking the device automatically to block unauthorized access.
How ActiveLock Continuous Endpoint Authentication helps you achieve BYOD Security
TypingDNA ActiveLock is a continuous endpoint authentication solution based on patented typing biometrics technology. It works by analyzing the device user’s typing patterns against previous samples of the authorized employee. It prevents device sharing and makes sure each person in front of the computer is always the genuine authorized user.
With ActiveLock, any company can benefit from real-time defense against fraudulent device sharing of BYOD devices while having a privacy-focused approach that examines HOW the user types but never WHAT they type.
Get your complimentary ActiveLock license to see how continuous authentication can secure BYOD devices.

