Insider threats include individuals within an organization who purposely or by mistake expose company information. Because proprietary data, customer information, and trade secrets are the heart and soul of any enterprise, security systems and processes to reduce insider threats are essential.
Surprisingly, most insider threats result from negligent employees, such as those working remotely, who might “innocently” share their laptops with friends. But because these friends can click on a phishing link anytime, solutions to protect the endpoint from unauthorized users become essential for enterprise security.
Below we look at the types of insider threats and how to approach this issue from an organizational perspective. Because employees and contractors are harder to monitor in a remote environment, we’ll also explore how continuous endpoint authentication can reduce the risk of insider threats, especially in work-from-home scenarios.
Table of Contents:
What are the three types of insider threats?
How to prevent & respond to insider threats
How Continuous Endpoint Authentication (CEA) reduces insider threats
What are insider threats?
In cybersecurity, insider threats are the risks posed to data security by individuals from within an organization. People remain at the center of this issue because they have authorized access to and knowledge of an organization’s resources, facilities, information, networks, and systems.
Examples of insiders are:
- People trusted within the organization, such as employees with access to sensitive information.
- External people trusted by the organization with regular or continuous access to sensitive information, like contractors, vendors, custodians, or repair professionals.
- Anyone with access to a company’s network and systems.
- People who know sensitive information regarding the corporation, such as costs, pricing, structural strengths, weaknesses, and competitive advantages.
- Persons trusted by the organization for product or service development who have access to confidential plans and company goals.
An insider threat could backstab the company for any number of malicious incentives — like when a trusted employee shares company secrets with competitors for financial gain. But insider threats are not always bad-intended or malicious. An authorized employee can innocently share their work devices with a household member who can click on a phishing link by mistake. Or, an employee can lose their work login credentials, leading to imposters being able to breach those accounts and steal confidential company information.
Let’s take a closer look at the types of insider threats and the reasons behind them.
What are the three types of insider threats?
Intent plays the most critical role in categorizing insider threats. Insider threats are usually classified into three categories depending on the reason behind the harm done to the company: complacent, hostile, or unintentional. Let’s explore each scenario.
Negligent insiders are complacent authorized users
Negligent insiders are people whose access to private company data is misused to harm the organization but without their intent or any premeditation. And while negligence might not be intentional, disregarding corporate security and well-being can be just as harmful as deliberate theft.
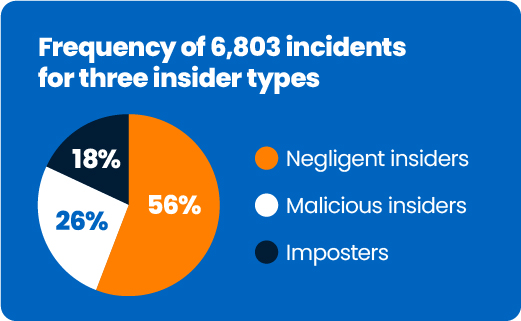
Though not hostile, negligent insiders often cause harmful consequences by not following organizational security policies. They can be responsible for engaging in device sharing, sharing login credentials, or simply leaving their work devices unlocked and unattended for imposters to take over. Statistics show that insider threats caused by careless employees are the most prevalent of all types of insider threats — generating 56% of insider threat incidents.
However, only 21% of organizations that responded to the Cost of Insider Threats report are concerned about negligent insiders. This shows that organizations are not yet prepared to accept the increase in “relaxed” attitudes among employees and consequently not taking enough action to reduce the risks of careless insider threats.
Malicious insiders are hostile authorized users
Malicious insiders intentionally use their authorized access to private company information to harm the organization by selling the information to the highest bidder or making it available to the public.
The reasons a contractor, employee, or partner would turn out to become a malicious insider are similar to why people do anything terrible in general. Malicious insiders are motivated by revenge, hate, or simply for financial gain to justify why they engage in illegal activities — including corporate espionage, unauthorized disclosure of information, and sabotage.
Yet interestingly, according to the report by Ponemon Institute, in 2022, only 26% of insider threat incidents were caused by malicious insiders. So if negligent insiders own an almost double percentage at 56% of all insider threats, are companies focusing too much on malicious insiders instead of finding solutions to the more prevalent day-to-day issues that happen out of employee negligence, such as device sharing?
Credential theft happens because of hostile imposter users
Credential thieves, known as infiltrators or imposters, are external people who steal the credentials of legitimate employees or contractors to gain access to corporate information by force. A favorite technique for many credential thieves is social engineering attacks, such as phishing. Although, in reality, credential thieves make up only 18% of all insider threats, a whopping 55% of organizations prioritize worrying about imposters or infiltrators.
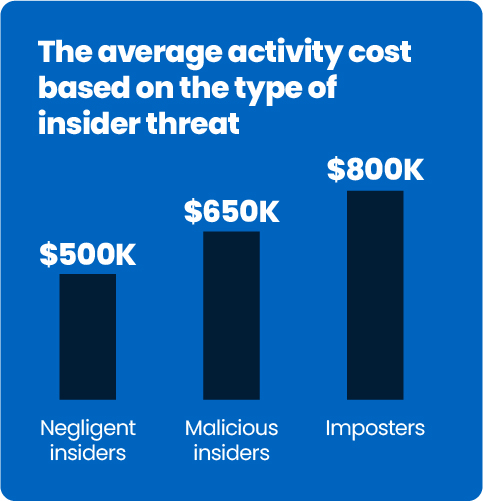
Regardless of the type of insider threat, the actions organizations need to take to navigate such incidents after they take place often come with massive expenses. The average activity cost per incident ranges from ~$500,000 for insider threats related to employee or contractor negligence to ~$800,000 for credential theft incidents. The takeaway? Employee negligence seems to be the type of insider threat that is cheaper to navigate despite being the most prevalent. While malicious threats are less prevalent but more expensive to deal with.
With such high costs of mitigating the effects of insider threats and large prevalence percentages, what can companies do to detect those risks before they take place?
How to detect insider threats
Both technological and human elements are essential to watch out for to detect insider threats. You need to be able to observe the concerning behaviors of employees and external parties related to how they use their authorized access to company data and resources.
Depending on the type of insider threat, the particularities of each situation change. For malicious insiders, personal factors are the prime reasons that may prompt them to undergo criminal activity within an organization. Some examples of individual factors may include issues at work and job dissatisfaction, greed, financial need, anger, divided loyalty, and family problems.
Whatever these “reasons” are, organizational factors like the poor implementation of security policies increase the ease with which insiders may steal proprietary data. So, having a clear view of what these security practices mean for your organization is critical in determining the risk of insider threats. Monitoring and surveillance include technologies that enhance mitigation and early detection, enabling an organization to detect and potentially deter insider threats. One way to detect insider threats is to have continuous endpoint authentication on company devices.
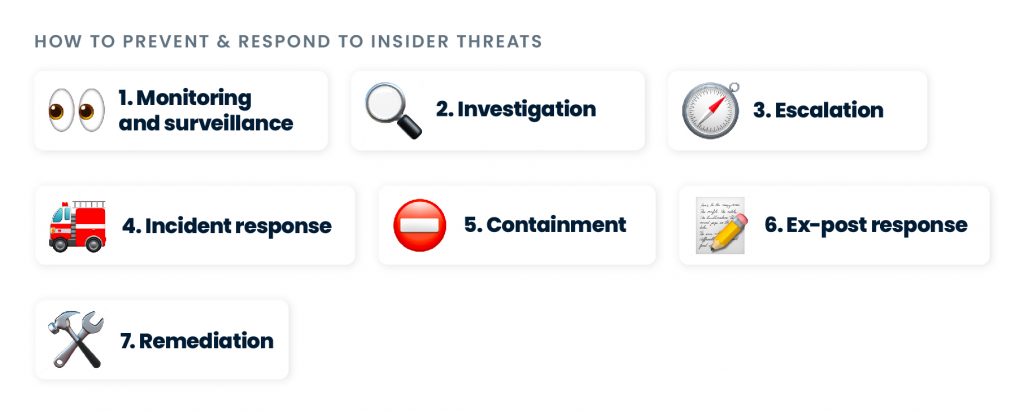
Here are 7 steps you can take to detect insider threats
⛔️ Prevent simultaneous logins from a single user by limiting the number of access points and login sessions an employee can have at one time.
🔍 Control how users access the company’s network and assets by setting up login controls to only allow certain login attempts, depending on the location, time of day, and session type.
🔑 Implement Privileged Access Management (PAM) solutions to give the workforce only the system access they need to perform their particular job and complete their job-related tasks.
🛡 Monitor file access events and have systems in place to alert suspicious activity, such as when an employee is denied access to a file or when a file event takes place outside work hours.
⚙️ Build a security architecture and train employees to follow security guidelines appropriately. But that’s not enough, so try to routine test if employees follow those rules, for example, by sending out a mock phishing email to see if lessons were learned.
🔒 Implement a zero trust approach and have Multi-Factor Authentication (MFA) as a requirement for any login attempts on endpoints and company accounts like Hubspot, email, or Google Drive.
✅ Have continuous endpoint authentication (CEA) on your employees’ devices to tell when work devices are being shared with outside parties or accessed by unauthorized users, especially if you have a remote workforce.
How to prevent & respond to insider threats
Organizations must put in place a thorough security strategy for insider threats. From the time an incident occurs to after the damage has been done, the risk of insider threats must be monitored, contained, and remediated. A strategy to prevent insider threats could mean implementing the following processes:
- Monitoring and surveillance – relate to the implementation of a variety of security practices to ensure only authorized users access company resources, such as Data Loss Prevention (DLP), Privileged Access Management (PAM), Security Information and Event Management (SIEM), Endpoint Detection and Response (EDR), and Insider Threat Management (ITM), just to name a few.
- Investigation – are all the activities required to analyze and uncover the origins, reasons behind, and extent of one or more insider threat incidents.
- Escalation – are all the activities needed to raise awareness about specific incidents among stakeholders, including steps taken to organize the initial threat management response.
- Incident response – are all the actions taken by the incident response team to formulate the final management response.
- Containment – relates to the actions aimed at lowering the impact of the attacks, such as closing certain vulnerable business operations or blocking compromised company endpoints.
- Ex-post response – are all the steps required to minimize future potential insider threats, like communicating with stakeholders or designing suggestions to mitigate the risk of future insider threats.
- Remediation – repairing systems, restoring the security infrastructure, and restarting business processes that management shut down during containment are examples of remediation activities.
Insider threat management team
The Cybersecurity and Infrastructure Agency recommends forming a multi-disciplinary threat management team to cope with insider threats by managing the mitigation process. Training is essential to develop the team and should include courses on threat assessment, legal considerations, and health and safety aspects.
Any assets involved in the insider threat mitigation process should collaborate with the ultimate objective to protect the organization and its people. The team should engage internal and external stakeholders such as employees, collaborators, external threat analysts, and other trusted sources.
How to reduce careless or negligent insider threats in a remote workforce with Continuous Endpoint Authentication (CEA)
Careless or negligent insider threats are higher in a remote workforce
In remote environments, human error accounts for 23% of data breaches. IBM’s recent report on how much data breaches cost in 2022 shows that the increase in remote work practices has changed the cybersecurity landscape. The average data breach cost was over a million dollars higher when employees worked remotely compared to breaches in which working remotely was not a factor. The hidden (security) cost of remote work has much to do with employee negligence.
Yes, security systems and practices and security training for employees are crucial. But implementing those strategies will not prevent endpoints from being accessed by outside parties other than the trusted employees.
The risk of insider threat will still be higher in remote environments. Because the unfortunate truth is that negligent employees will share work devices and leave work devices unlocked and unattended, regardless of how much you tell them not to.
Why does CEA reduce the risk of insider threats?

CEA, or Continuous Endpoint Authentication, reduces the risk of insider threats because it stops an endpoint from being used by anyone other than the authorized employee. CEA gives IT teams the peace of mind that endpoints are in the right hands — and alerts them in case of unauthorized access.
Continuous endpoint authentication with passive behavioral biometrics
Continuous endpoint authentication solutions are plenty, and some of the most popular include facial recognition and fingerprint scanning, but these methods are expensive and difficult to implement. In the case of facial recognition, not only is it expensive for the organization, but it’s also highly invasive for employees — so in case you are using it, STOP.
A behind-the-scenes and user-friendly authentication solution is typing biometrics, a passive behavioral biometrics technology that recognizes users by how they type. TypingDNA ActiveLock is a Continuous Endpoint Authentication application that analyzes user behavior, mainly focusing on typing patterns. TypingDNA ActiveLock analyzes how an employee types throughout their login session to lock the computer in case someone else takes over, effectively reducing the chance of unauthorized users getting ahold of confidential information.
To sum it all up…
Companies must improve their security posture in several ways to maximize security when their workforce is remote. One of the first things on the list is to increase employees’ access to networks, systems, apps, and sensitive information.
But, building the proper security infrastructure to secure how employees interact with files and systems takes time, especially when the workforce is working remote and out-of-sight. It is a lengthy and, unfortunately, unavoidable process. So, a strategic approach for IT teams to quickly and efficiently decrease the risk of insider threats is to add continuous endpoint authentication (CEA) solutions to all company endpoints.
CEA solutions like ActiveLock will give around-the-clock insights if unauthorized parties access any corporate devices. This will put any IT team steps ahead of all three types of insider threats —malicious, negligent, and credential thieves— increasing the security of company data found on remote corporate endpoints.