Blog

InActiveLock Continuous Endpoint Authentication (CEA)AIBehavioral BiometricsBuilt with TypingDNAFAQs SeriesTyping Biometrics
FAQs – What is typing biometrics?
What is typing biometrics technology? It is embedded in peoples’ transient behavior when typing on a keyboard. See how it works, here.
Types of behavioral biometrics: Mouse use characteristics
Biometrics represent uniquely identifying and measurable patterns in human interaction with devices such as the mouse use characteristics.
A quick guide to choosing multi-factor authentication methods
In a world with an increasing amount of cyber threats, the question posed is no longer whether we need authentication. The real question is how to choose the right MFA methods to suit your security needs, and this is the focus of this blog post.
PSD2: EBA’s Opinion on SCA elements as of June 2019
The new Payment Services Directive – PSD2 is meant to better the current state of the European financial markets, adapt to the technological advancements of recent years, and propose up-to-date, common standards across the EU.
A review of the evolution of multi-factor authentication (MFA)
The evolution of MFA methods changed the face of cybersecurity. Technological developments promise affordable and user-friendly MFA.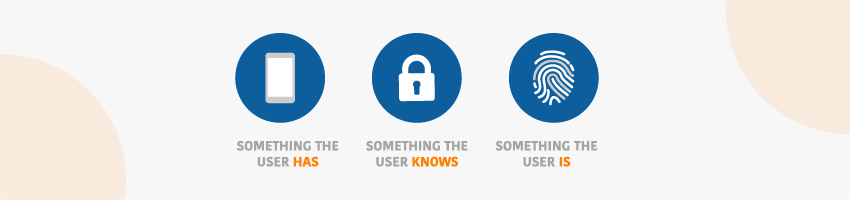
EBA approves typing biometrics in SCA of PSD2
The European Banking Authority clarifies on what constitutes a compliant element in each of the three possible categories of multi-factor authentication: inherence, possession, and knowledge. EBA approves typing biometrics as compliant to be used in multi-factor authentication.
Common drawbacks of multi-factor authentication
MFA brings forth strong layers of security, helps companies achieve compliance, and increases flexibility and productivity by removing the burden of passwords.
Significant MFA deployment factors to look for
Implementing MFA comes with multiple benefits like high security (one factor is not enough), better access control and compliance with regulations in various industries.